index
Set up authentication config from browser network logs
info
This feature is currently available only to selected organizations.
This document describes how to set up the "automatic login before diagnosis" feature in Shisho Cloud using a HAR file containing the network logs generated by the login operation.
Capture network logs from your browser
Steps for Google Chrome
Use incognito mode to perform the following steps.
Set up developer tools
- Open Developer Tools.
- Click the gear icon in the top right to open the settings.
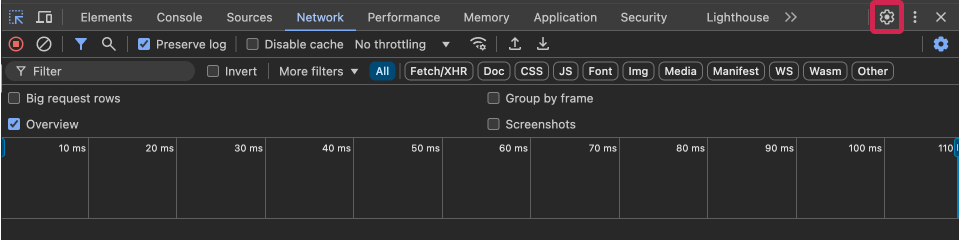
- Scroll down to the "Network" section.
- Check the "Allow to generate HAR (with sensitive data)" box.
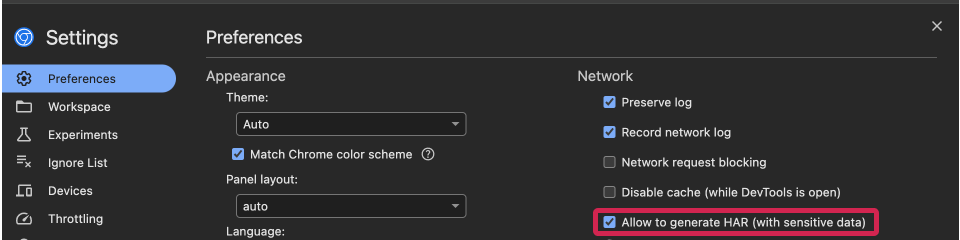
- Close the settings.
info
You need to include sensitive data such as cookies in order to use this information to set up the "automatic login before diagnosis" feature.
Prepare for traffic capture
Before accessing the application to be diagnosed, please make the following preparations:
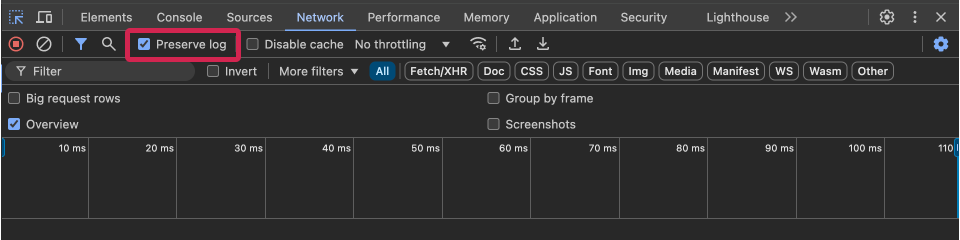
- Open the Network tab of Developer Tools in incognito mode.
- Check the Preserve log checkbox.
Access the application to be diagnosed and log in
- Open the login page.
- Enter your username, password, etc. and log in.
Save network logs
- Long-press the save button at the top right of the Network tab of Developer Tools to display two options: "Export HAR (sanitized)" and "Export HAR (with sensitive data)".
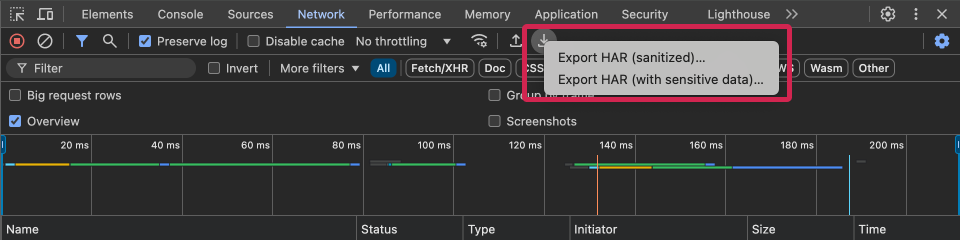
- Select "Export HAR (with sensitive data)".
- Save the file to the directory of your choice.
Upload HAR file
- In the Login Process Settings screen, import the downloaded HAR file.
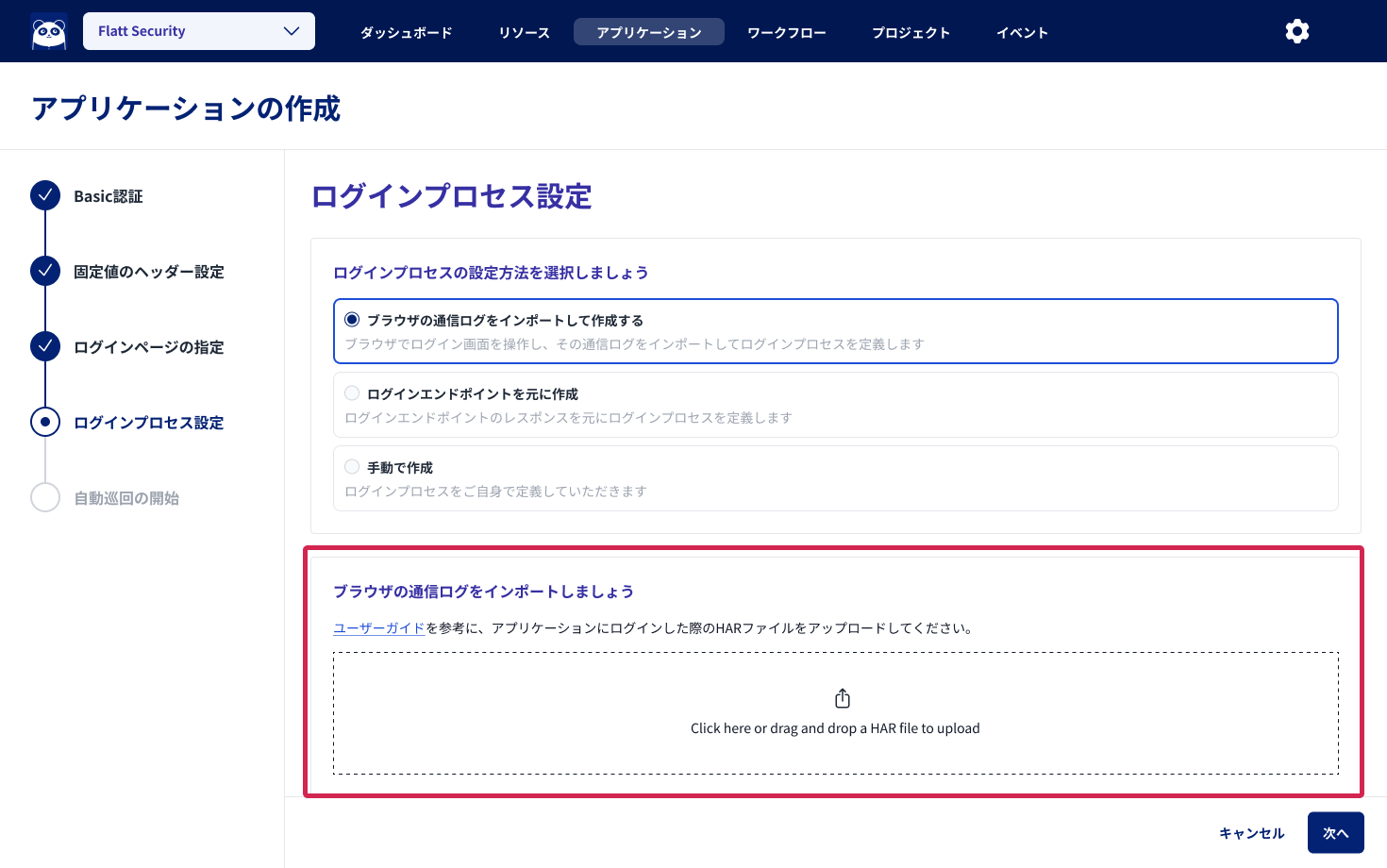
- The authentication definitions will be automatically generated based on the network logs.
- Use the "Connectivity Check" function to verify that the login process can be reproduced correctly.
- If the login is not successful, please modify the generated definition.
- It is recommended to remove any unnecessary authentication steps. (This will allow for faster authentication.)