Triage Issues
The English user guide is currently in beta preview. Most of the documents have been automatically translated from the Japanese version. Should you find any inaccuracies, please reach out to Flatt Security.
Efforts in security encompass continuous risk discovery and a dual-pronged approach of persistent risk reduction and resolution. Now that the initial setup of Shisho Cloud is complete, let's put the everyday workflow of grasping and resolving risks into practice.
Identifying What Needs Attention
After checking the inspection results produced by Shisho Cloud, take a look at the Evaluation Results section on your Dashboard. By default, this area lists important detection items (violations of policies) based on their priority level:
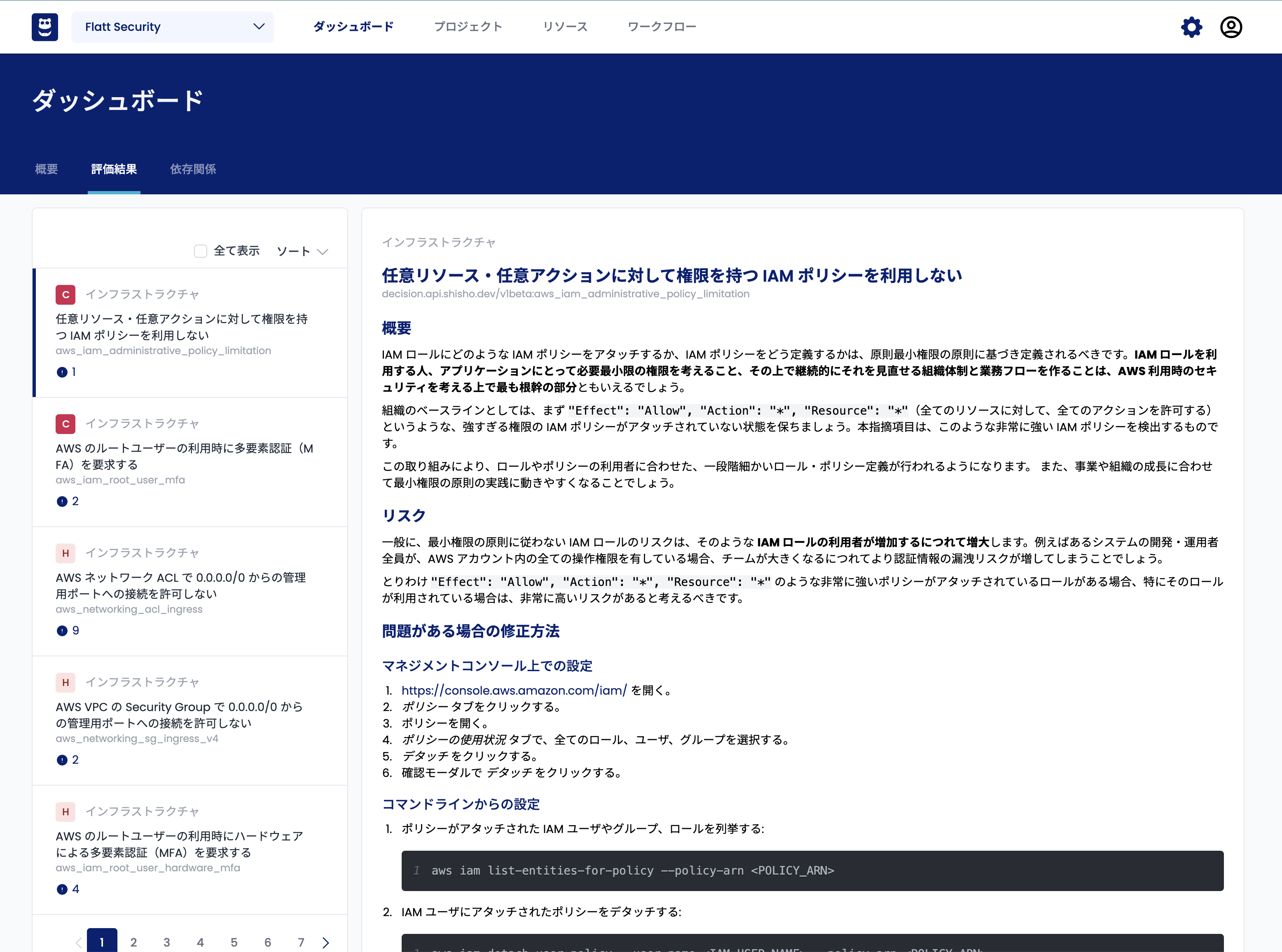
Here, you can learn about the following aspects of the identified security issues and recommendations:
- The nature of the problems in detail
- The related risks
- Guidance and tips for remediation
Determining a Triage Policy
Once you have identified the detected security issues and recommendations, it's time to consider how to handle them. In Shisho Cloud, every newly detected item is always marked as Awaiting Review. From here, you can choose one of the following three strategies:
- Mark it for action
- Accept the risk until a certain deadline
- Accept the risk without any action:
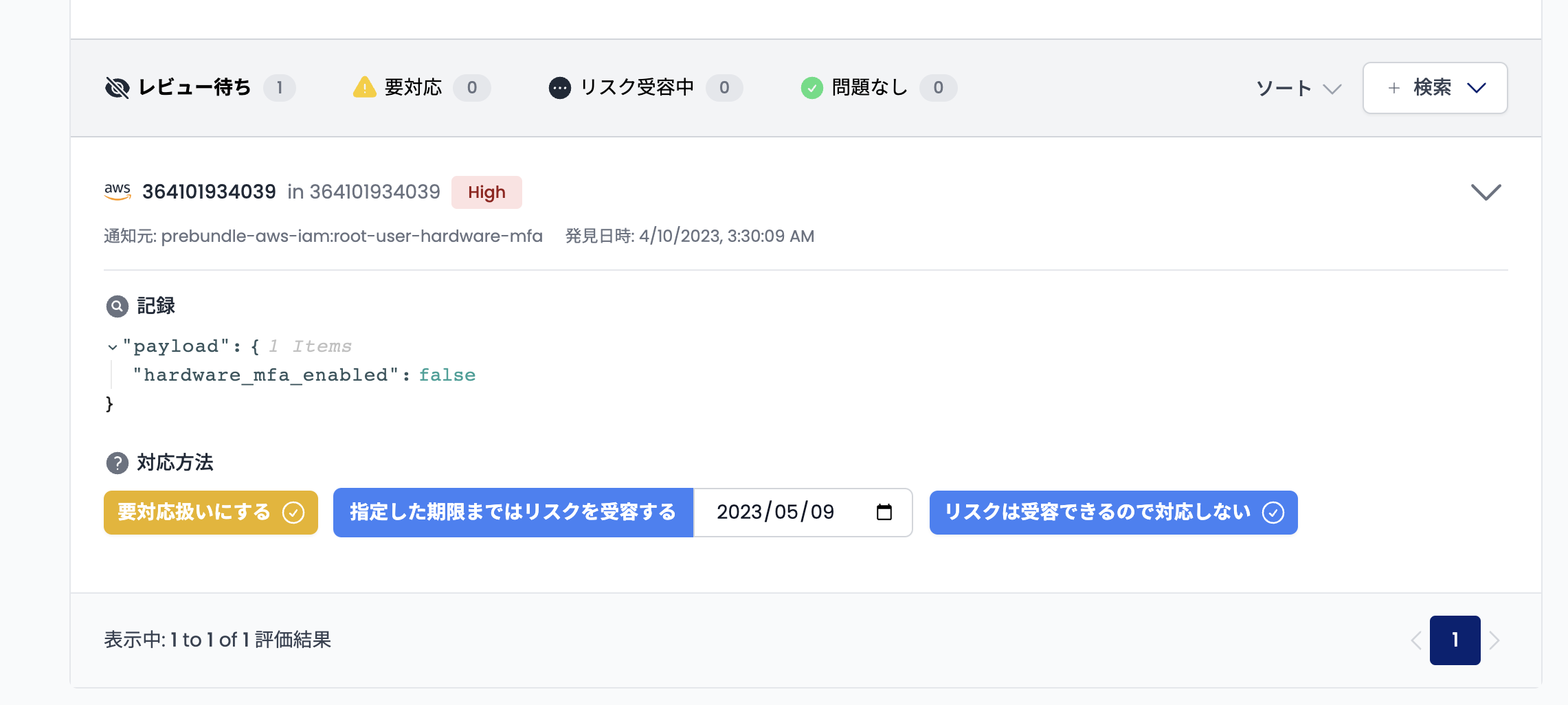
Upon selection, the detected item will transition to one of the following states:
- Awaiting Review
- Action Required
- Risk Accepted (With Deadline)
- Risk Accepted (Indefinite)
It's best to distinguish between issues in the Awaiting Review and Action Required states, which your organization should actively address, and those in the Risk Accepted states, which can be set aside for now.
On the dashboard, where various statistics are shown, only items in the Awaiting Review and Action Required states are displayed. A separate dashboard is planned to display the total quantity of detected items where the risk has been accepted.
Sharing Triage Information via Notifications
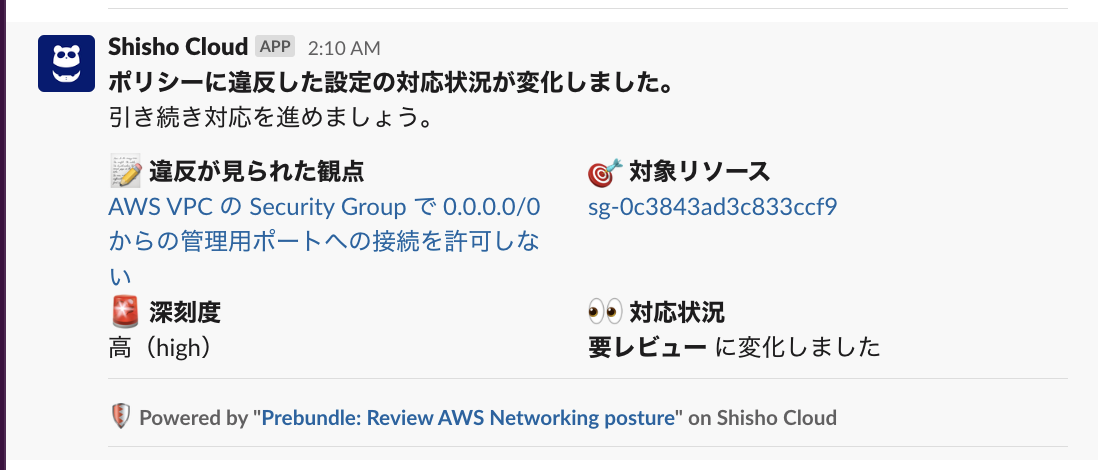
The process of triaging issues of a minimum urgency level or more, as specified in the Notification Settings, will also be sent to various destinations.
Example Slack Notification
Example Email Notification

In the Notification Workflow editing page, you can also narrow down triage notifications by editing the triggers section:
triggers:
triage:
# send notifications when...
- event: [updated]
status_changed_to:
# the issue is calling your review.
- awaiting_review
# the issue is acknowledged, and no further action is expected.
- acknowledged
# the issue is flagged for your action.
- action_required
# the issue was resolved :tada:
- secure
# the resource with security issue(s) gets deleted.
- deleted
# send notifications on a finding that needs your action
- event: [created]
status_changed_to:
- awaiting_review
For instance, if you want to receive notifications only when new risks are detected or when risks are mitigated by changes or removals, you can do so by editing the triggers section this way:
triggers:
triage:
# send notifications when...
- event: [updated]
status_changed_to:
# the issue was resolved :tada:
- secure
# the resource with security issues gets deleted.
- deleted
# send notifications on a finding that needs your action
- event: [created]
status_changed_to:
- awaiting_review