Google Cloud
The English user guide is currently in beta preview. Most of the documents have been automatically translated from the Japanese version. Should you find any inaccuracies, please reach out to Flatt Security.
By integrating Shisho Cloud and Google Cloud, you can perform security scans on your Google Cloud projects and organizations. This integration can be done in the following three steps:
- Create a service account that Shisho Cloud can impersonate and the associated resources.
- Grant the created service account the necessary permissions to perform security inspections on the Google Cloud project.
- Register the information of the created service account and related resources with Shisho Cloud.
Creation of the Service Account and Related Resources
First, create a service account, identity pool, and identity provider in any Google Cloud project for use from Shisho Cloud, following one of the procedures below.
Even if you want to inspect multiple Google Cloud projects, this process only needs to be done once. That is, you only need one service account, identity pool, and identity provider for Shisho Cloud.
- gcloud CLI
- Terraform
- Web Console (Cloud Shell)
After changing the values in the # Input values section at the beginning of the script appropriately, run the following script to create the necessary resources (ID provider and IAM roles):
#!/bin/bash
set -eu
# Input values
############
# Google Cloud Project ID
PROJECT_ID="your-google-cloud-project-id"
# Shisho Cloud Organization ID
SHISHO_ORG_ID="you-shisho-organization-id"
# ID of the identity pool to be created; no need to change unless there's a specific reason
POOL_ID="shisho-cloud"
# ID of the identity provider to be created; no need to change unless there's a specific reason
PROVIDER_ID="shisho-cloud"
# Name of the service account to be created; no need to change unless there's a specific reason
SERVICE_ACCOUNT_NAME="shisho-cloud"
# Creation
############
TOKEN_ENDPOINT_URL="https://tokens.cloud.shisho.dev"
PROJECT_NUMBER="$(gcloud projects describe $PROJECT_ID --format="value(projectNumber)")"
# Ensure to enable APIs that needs to be enabled on the project that includes the service account to integrate with Shisho Cloud.
gcloud services enable \
bigquery.googleapis.com \
cloudasset.googleapis.com \
cloudkms.googleapis.com \
cloudresourcemanager.googleapis.com \
compute.googleapis.com \
container.googleapis.com \
dns.googleapis.com \
essentialcontacts.googleapis.com \
logging.googleapis.com \
iamcredentials.googleapis.com \
iam.googleapis.com \
pubsub.googleapis.com \
serviceusage.googleapis.com \
storage-component.googleapis.com \
sqladmin.googleapis.com \
--project "$PROJECT_ID"
# Create a Workload Identity Pool & Provider
gcloud iam workload-identity-pools create "$POOL_ID" \
--project="$PROJECT_ID" \
--description="An identity pool for Shisho Cloud audit jobs. Visit https://shisho.dev/docs/ja/g/getting-started/integrate-apps/googlecloud for further details." \
--location=global \
--display-name="$POOL_ID"
gcloud iam workload-identity-pools providers create-oidc "$PROVIDER_ID" \
--project="$PROJECT_ID" \
--location="global" \
--workload-identity-pool="$POOL_ID" \
--description="An identity provider for Shisho Cloud audit jobs. Visit https://shisho.dev/docs/ja/g/getting-started/integrate-apps/googlecloud for further details." \
--display-name="$PROVIDER_ID" \
--attribute-mapping="google.subject=assertion.sub,attribute.organization_id=assertion.organization_id,attribute.workflow_id=assertion.workflow_id,attribute.job_id=assertion.job_id" \
--attribute-condition="assertion.organization_id == '$SHISHO_ORG_ID'" \
--issuer-uri="$TOKEN_ENDPOINT_URL"
# Create a service account that can be impersonated IDs in the pool
gcloud iam service-accounts create "$SERVICE_ACCOUNT_NAME" \
--description="A service account that Shisho Cloud impersonates and use for listing up projects, resources, and their settings. Visit https://shisho.dev/docs/ja/g/getting-started/integrate-apps/googlecloud for further details." \
--project "$PROJECT_ID"
gcloud iam service-accounts add-iam-policy-binding "$SERVICE_ACCOUNT_NAME@$PROJECT_ID.iam.gserviceaccount.com" \
--project="$PROJECT_ID" \
--role="roles/iam.workloadIdentityUser" \
--member="principalSet://iam.googleapis.com/projects/$PROJECT_NUMBER/locations/global/workloadIdentityPools/$POOL_ID/*"
# Post-processing
echo "Visit https://cloud.shisho.dev/${SHISHO_ORG_ID}/settings/integrations/googlecloud and add a federation with:"
echo "- Service Account Email: ${SERVICE_ACCOUNT_NAME}@${PROJECT_ID}.iam.gserviceaccount.com"
echo "- Pool Project Number: ${PROJECT_NUMBER}"
echo "- Pool ID: ${POOL_ID}"
echo "- Provider ID: ${PROVIDER_ID}"
After the execution is complete, information about the following created resources will be output after Visit https://cloud.shisho.dev ....
Please keep this information for use in the later step "Registering information to Shisho Cloud".
- A service account named
shisho-cloud - An identity provider named
shisho-cloud - An identity pool named
shisho-cloud
After changing the value of variable shisho_cloud_org_id to the ID of your Shisho Cloud organization, include the following Terraform implementation in your Terraform project and then run terraform apply.
The sample code assumes that you have specified the Google Cloud project ID to create the service account, etc., in the project variable defined as follows:
variable "project" {
type = string
}
If such a variable is defined under a different name, please replace the references to var.project in the sample code as needed.
If such a variable is not defined, set the GOOGLE_PROJECT environment variable and either use the sample code after removing var.project or replace var.project directly with the project ID.
locals {
# Please change the following to your Shisho Cloud organization ID:
shisho_cloud_org_id = "your-shisho-organization-id"
}
# Ensure to enable APIs that needs to be enabled on the project that includes the service account to integrate with Shisho Cloud.
resource "google_project_service" "bigquery" {
project = var.project
service = "bigquery.googleapis.com"
}
resource "google_project_service" "cloudasset" {
project = var.project
service = "cloudasset.googleapis.com"
}
resource "google_project_service" "cloudkms" {
project = var.project
service = "cloudkms.googleapis.com"
}
resource "google_project_service" "resourcemanager" {
project = var.project
service = "cloudresourcemanager.googleapis.com"
}
resource "google_project_service" "compute" {
project = var.project
service = "compute.googleapis.com"
}
resource "google_project_service" "container" {
project = var.project
service = "container.googleapis.com"
}
resource "google_project_service" "dns" {
project = var.project
service = "dns.googleapis.com"
}
resource "google_project_service" "essentialcontacts" {
project = var.project
service = "essentialcontacts.googleapis.com"
}
resource "google_project_service" "logging" {
project = var.project
service = "logging.googleapis.com"
}
resource "google_project_service" "iamcredentials" {
project = var.project
service = "iamcredentials.googleapis.com"
}
resource "google_project_service" "iam" {
project = var.project
service = "iam.googleapis.com"
}
resource "google_project_service" "pubsub" {
project = var.project
service = "pubsub.googleapis.com"
}
resource "google_project_service" "serviceusage" {
project = var.project
service = "serviceusage.googleapis.com"
}
resource "google_project_service" "storage-component" {
project = var.project
service = "storage-component.googleapis.com"
}
resource "google_project_service" "sqladmin" {
project = var.project
service = "sqladmin.googleapis.com"
}
# Create a service account
resource "google_service_account" "shisho_cloud" {
project = var.project
account_id = "shisho-cloud"
description = "A service account that Shisho Cloud impersonates and use for listing up projects, resources, and their settings. Visit https://shisho.dev/docs/ja/g/getting-started/integrate-apps/googlecloud for further details."
}
# Create an identity pool
resource "google_iam_workload_identity_pool" "shisho_cloud" {
project = var.project
workload_identity_pool_id = "shisho-cloud"
description = "An identity pool for Shisho Cloud audit jobs. Visit https://shisho.dev/docs/ja/g/getting-started/integrate-apps/googlecloud for further details."
}
# Create an identity provider
resource "google_iam_workload_identity_pool_provider" "shisho_cloud" {
project = var.project
workload_identity_pool_provider_id = "shisho-cloud"
workload_identity_pool_id = google_iam_workload_identity_pool.shisho_cloud.workload_identity_pool_id
description = "An identity provider for Shisho Cloud audit jobs. Visit https://shisho.dev/docs/ja/g/getting-started/integrate-apps/googlecloud for further details."
oidc {
issuer_uri = "https://tokens.cloud.shisho.dev"
}
attribute_mapping = {
"google.subject" = "assertion.sub"
"attribute.organization_id" = "assertion.organization_id"
"attribute.workflow_id" = "assertion.workflow_id"
"attribute.job_id" = "assertion.job_id"
}
# Limit the scope of the service account to only be able to access the
attribute_condition = "attribute.organization_id == '${local.shisho_cloud_org_id}'"
}
# Grant the identity from the identity provider to impersonate the service account
resource "google_service_account_iam_member" "shisho_cloud_iam_workload_identity_user" {
service_account_id = google_service_account.shisho_cloud.id
role = "roles/iam.workloadIdentityUser"
member = "principalSet://iam.googleapis.com/${google_iam_workload_identity_pool.shisho_cloud.name}/*"
}
Upon completion, the following should have been created:
- A service account named
shisho-cloud - An identity provider named
shisho-cloud - An identity pool named
shisho-cloud
Launch Cloud Shell from the terminal button in the upper right corner of the screen. It is the button highlighted in the upper right corner of the following image:

After clicking and waiting for a while, Cloud Shell will start up as shown below, and the gcloud command will be available:

After changing the value in the # ID of the Shisho Cloud organization you created section at the beginning appropriately, copy and paste the following script into the Cloud Shell and execute it to create the necessary resources (ID provider and IAM roles):
# Shisho Cloud Organization ID
SHISHO_ORG_ID="you-shisho-organization-id"
# ID of the identity pool to be created; no need to change unless there's a specific reason
POOL_ID="shisho-cloud"
# ID of the identity provider to be created; no need to change unless there's a specific reason
PROVIDER_ID="shisho-cloud"
# Name of the service account to be created; no need to change unless there's a specific reason
SERVICE_ACCOUNT_NAME="shisho-cloud"
TOKEN_ENDPOINT_URL="https://tokens.cloud.shisho.dev"
PROJECT_ID="$(gcloud config get-value project)"
PROJECT_NUMBER="$(gcloud projects describe $PROJECT_ID --format="value(projectNumber)")"
# Ensure to enable APIs that needs to be enabled on the project that includes the service account to integrate with Shisho Cloud.
gcloud services enable \
bigquery.googleapis.com \
cloudasset.googleapis.com \
cloudkms.googleapis.com \
cloudresourcemanager.googleapis.com \
compute.googleapis.com \
container.googleapis.com \
dns.googleapis.com \
essentialcontacts.googleapis.com \
logging.googleapis.com \
iamcredentials.googleapis.com \
iam.googleapis.com \
pubsub.googleapis.com \
serviceusage.googleapis.com \
storage-component.googleapis.com \
sqladmin.googleapis.com \
--project "$PROJECT_ID"
# Create a Workload Identity Pool & Provider
gcloud iam workload-identity-pools create "$POOL_ID" \
--project="$PROJECT_ID" \
--description="An identity pool for Shisho Cloud audit jobs. Visit https://shisho.dev/docs/ja/g/getting-started/integrate-apps/googlecloud for further details." \
--location=global \
--display-name="$POOL_ID"
gcloud iam workload-identity-pools providers create-oidc "$PROVIDER_ID" \
--project="$PROJECT_ID" \
--location="global" \
--workload-identity-pool="$POOL_ID" \
--description="An identity provider for Shisho Cloud audit jobs. Visit https://shisho.dev/docs/ja/g/getting-started/integrate-apps/googlecloud for further details." \
--display-name="$PROVIDER_ID" \
--attribute-mapping="google.subject=assertion.sub,attribute.organization_id=assertion.organization_id,attribute.workflow_id=assertion.workflow_id,attribute.job_id=assertion.job_id" \
--attribute-condition="assertion.organization_id == '$SHISHO_ORG_ID'" \
--issuer-uri="$TOKEN_ENDPOINT_URL"
# Create a service account that can be impersonated IDs in the pool
gcloud iam service-accounts create "$SERVICE_ACCOUNT_NAME" \
--description="A service account that Shisho Cloud impersonates and use for listing up projects, resources, and their settings. Visit https://shisho.dev/docs/ja/g/getting-started/integrate-apps/googlecloud for further details." \
--project "$PROJECT_ID"
gcloud iam service-accounts add-iam-policy-binding "$SERVICE_ACCOUNT_NAME@$PROJECT_ID.iam.gserviceaccount.com" \
--project="$PROJECT_ID" \
--role="roles/iam.workloadIdentityUser" \
--member="principalSet://iam.googleapis.com/projects/$PROJECT_NUMBER/locations/global/workloadIdentityPools/$POOL_ID/*"
# Post-processing
echo "Visit https://cloud.shisho.dev/${SHISHO_ORG_ID}/settings/integrations/googlecloud and add a federation with:"
echo "- (1) Service Account Email: ${SERVICE_ACCOUNT_NAME}@${PROJECT_ID}.iam.gserviceaccount.com"
echo "- (2) Pool Project Number: ${PROJECT_NUMBER}"
echo "- (3) Pool ID: ${POOL_ID}"
echo "- (4) Provider ID: ${PROVIDER_ID}"
After execution is complete, information about the following created resources will be output after Visit https://cloud.shisho.dev ....
Please keep this information for use in the later step "Registering information to Shisho Cloud".
- A service account named
shisho-cloud - An identity provider named
shisho-cloud - An identity pool named
shisho-cloud
Once the service account is created, make note of the created service account's email address.
The email address should look something like shisho-cloud@<project-name>.iam.gserviceaccount.com if you used the above scripts as they are.
Also, along with the service account's email address, please note the project number of the Google Cloud project where you created the service account and related resources. This is typically a 12-digit number and can be found on the welcome page of the Google Cloud console.
Granting Privileges to the Service Account
At this point, you are almost ready for Shisho Cloud to use the Google Cloud service account. Next, let's grant the service account the access rights to the actual targets you want to conduct security scans on.
If you want to manage the security of a single project
There may be cases where, instead of continuously inspecting an entire Google Cloud organization or folder with Shisho Cloud, you want to select projects and set access rights to Shisho Cloud for them. In this case, refer to the following code sample and grant the created service account the following roles for that project:
roles/iam.securityReviewer(Security Reviewer)roles/bigquery.metadataViewer(BigQuery Metadata Viewer)roles/orgpolicy.policyViewer(Organization Policy Viewer)roles/browser(Browser)roles/accessapproval.viewer(Access Approval Viewer)roles/firebaseauth.viewer(Firebase Authentication Viewer)roles/serviceusage.serviceUsageConsumer(Service Usage Consumer)roles/compute.viewer(Compute Viewer)
The roles granted here basically allow you to read only the configuration values of resources, and in principle, do not include permission to view data in data storage (Cloud Storage, Cloud SQL, etc.). However, the compute.viewer role exceptionally includes access to VM screenshots and serial port output. If this is not desired, you can choose not to grant the permission, but some features may not work. If you want to check the detailed permissions included in a role, please refer to the Google Cloud official documentation.
- gcloud CLI
- Terraform
- Web Console
After checking the value in the Input values section, you can grant permission to the service account by running the following command:
#!/bin/bash
set -eu
# Input values
############
# Google Cloud Project ID where the created service account resides
PROJECT_ID="your-google-cloud-project-id"
# Service account name you created; leave as is if you ran the above script as is
SERVICE_ACCOUNT_NAME="shisho-cloud"
# Grant permissions
############
gcloud projects add-iam-policy-binding "$PROJECT_ID" \
--role="roles/iam.securityReviewer" \
--condition=None \
--member="serviceAccount:$SERVICE_ACCOUNT_NAME@$PROJECT_ID.iam.gserviceaccount.com"
gcloud projects add-iam-policy-binding "$PROJECT_ID" \
--role="roles/bigquery.metadataViewer" \
--condition=None \
--member="serviceAccount:$SERVICE_ACCOUNT_NAME@$PROJECT_ID.iam.gserviceaccount.com"
gcloud projects add-iam-policy-binding "$PROJECT_ID" \
--role="roles/orgpolicy.policyViewer" \
--condition=None \
--member="serviceAccount:$SERVICE_ACCOUNT_NAME@$PROJECT_ID.iam.gserviceaccount.com"
gcloud projects add-iam-policy-binding "$PROJECT_ID" \
--role="roles/browser" \
--condition=None \
--member="serviceAccount:$SERVICE_ACCOUNT_NAME@$PROJECT_ID.iam.gserviceaccount.com"
gcloud projects add-iam-policy-binding "$PROJECT_ID" \
--role="roles/accessapproval.viewer" \
--condition=None \
--member="serviceAccount:$SERVICE_ACCOUNT_NAME@$PROJECT_ID.iam.gserviceaccount.com"
gcloud projects add-iam-policy-binding "$PROJECT_ID" \
--role="roles/firebaseauth.viewer" \
--condition=None \
--member="serviceAccount:$SERVICE_ACCOUNT_NAME@$PROJECT_ID.iam.gserviceaccount.com"
gcloud projects add-iam-policy-binding "$PROJECT_ID" \
--role="roles/serviceusage.serviceUsageConsumer" \
--condition=None \
--member="serviceAccount:$SERVICE_ACCOUNT_NAME@$PROJECT_ID.iam.gserviceaccount.com"
When setting roles in Terraform, you can grant roles with the google_project_iam_member resource as follows:
// Assuming:
// resource "google_service_account" "shisho_cloud" {
// project = var.project
// account_id = "shisho-cloud"
// description = "A service account that Shisho Cloud impersonates and use for listing up projects, resources, and their settings. Visit https://shisho.dev/docs/ja/g/getting-started/integrate-apps/googlecloud for further details."
// }
resource "google_project_iam_member" "shisho_cloud_project_security" {
project = var.project
role = "roles/iam.securityReviewer"
member = "serviceAccount:${google_service_account.shisho_cloud.email}"
}
resource "google_project_iam_member" "shisho_cloud_project_bigquery" {
project = var.project
role = "roles/bigquery.metadataViewer"
member = "serviceAccount:${google_service_account.shisho_cloud.email}"
}
resource "google_project_iam_member" "shisho_cloud_org_policy" {
project = var.project
role = "roles/orgpolicy.policyViewer"
member = "serviceAccount:${google_service_account.shisho_cloud.email}"
}
resource "google_project_iam_member" "shisho_cloud_browser" {
project = var.project
role = "roles/browser"
member = "serviceAccount:${google_service_account.shisho_cloud.email}"
}
resource "google_project_iam_member" "shisho_cloud_access_approval" {
project = var.project
role = "roles/accessapproval.viewer"
member = "serviceAccount:${google_service_account.shisho_cloud.email}"
}
resource "google_project_iam_member" "shisho_cloud_firebase_auth" {
project = var.project
role = "roles/firebaseauth.viewer"
member = "serviceAccount:${google_service_account.shisho_cloud.email}"
}
resource "google_project_iam_member" "shisho_cloud_service_usage" {
project = var.project
role = "roles/serviceusage.serviceUsageConsumer"
member = "serviceAccount:${google_service_account.shisho_cloud.email}"
}
Open the IAM & Admin console, and if the project selector is displayed, select the project (or folder/organizational unit) you want to inspect. If it is not displayed, after the screen opens, select the project (or folder/organizational unit) you want to inspect from the part where the project name is displayed at the top of the screen. Then, you will see a screen like the one below:

Then click the "Grant Access" button. Then, you will see a screen like the one below:

After entering the following in the displayed screen, press the "Save" button:
- New principals: The address of the service account you created (e.g.,
shisho-cloud@<project name>.iam.gserviceaccount.com; if you used Cloud Shell or gcloud CLI when "Creating a Service Account", the value displayed afterService Account Email:) - Role: All of the following roles
roles/iam.securityReviewer(Security Reviewer)roles/bigquery.metadataViewer(BigQuery Metadata Viewer)roles/orgpolicy.policyViewer(Organization Policy Viewer)roles/browser(Browser)roles/accessapproval.viewer(Access Approval Viewer)roles/firebaseauth.viewer(Firebase Authentication Viewer)roles/serviceusage.serviceUsageConsumer(Service Usage Consumer)roles/compute.viewer(Compute Viewer)
If you want to manage the security of a folder or the entire Google Cloud organization
If you want Shisho Cloud to protect all projects in a folder or all projects included in your Google Cloud organization, grant the following roles for that folder/organization to the service account you created:
roles/iam.securityReviewer(Security Reviewer)roles/bigquery.metadataViewer(BigQuery Metadata Viewer)roles/orgpolicy.policyViewer(Organization Policy Viewer)roles/browser(Browser)roles/accessapproval.viewer(Access Approval Viewer)roles/firebaseauth.viewer(Firebase Authentication Viewer)roles/serviceusage.serviceUsageConsumer(Service Usage Consumer)roles/compute.viewer(Compute Viewer)
You can grant roles from the gcloud CLI, Terraform, or the web console, just like "If you want to manage the security of a single project."
For example, if you want to grant permissions at the organizational unit level, you can do the following:
- gcloud CLI
- Terraform
- Web Console
After checking the value in the Input Values section, you can grant permissions to the service account to your Google Cloud organization by running the following command:
#!/bin/bash
set -eu
# 入力値
############
# Google Cloud Project ID where the created service account resides
PROJECT_ID="your-google-cloud-project-id"
# Google Cloud Organization ID to review
# It should come from `gcloud organizations list`.
ORGANIZATION_ID="000000000000"
# Service account name you created; leave as is if you ran the above script as is
SERVICE_ACCOUNT_NAME="shisho-cloud"
# Grant permissions
############
gcloud organizations add-iam-policy-binding "$ORGANIZATION_ID" \
--role="roles/iam.securityReviewer" \
--condition=None \
--member="serviceAccount:$SERVICE_ACCOUNT_NAME@$PROJECT_ID.iam.gserviceaccount.com"
gcloud organizations add-iam-policy-binding "$ORGANIZATION_ID" \
--role="roles/bigquery.metadataViewer" \
--condition=None \
--member="serviceAccount:$SERVICE_ACCOUNT_NAME@$PROJECT_ID.iam.gserviceaccount.com"
gcloud organizations add-iam-policy-binding "$ORGANIZATION_ID" \
--role="roles/orgpolicy.policyViewer" \
--condition=None \
--member="serviceAccount:$SERVICE_ACCOUNT_NAME@$PROJECT_ID.iam.gserviceaccount.com"
gcloud organizations add-iam-policy-binding "$ORGANIZATION_ID" \
--role="roles/browser" \
--condition=None \
--member="serviceAccount:$SERVICE_ACCOUNT_NAME@$PROJECT_ID.iam.gserviceaccount.com"
gcloud organizations add-iam-policy-binding "$ORGANIZATION_ID" \
--role="roles/accessapproval.viewer" \
--condition=None \
--member="serviceAccount:$SERVICE_ACCOUNT_NAME@$PROJECT_ID.iam.gserviceaccount.com"
gcloud organizations add-iam-policy-binding "$ORGANIZATION_ID" \
--role="roles/firebaseauth.viewer" \
--condition=None \
--member="serviceAccount:$SERVICE_ACCOUNT_NAME@$PROJECT_ID.iam.gserviceaccount.com"
gcloud organizations add-iam-policy-binding "$ORGANIZATION_ID" \
--role="roles/serviceusage.serviceUsageConsumer" \
--condition=None \
--member="serviceAccount:$SERVICE_ACCOUNT_NAME@$PROJECT_ID.iam.gserviceaccount.com"
gcloud organizations add-iam-policy-binding "$ORGANIZATION_ID" \
--role="roles/compute.viewer" \
--condition=None \
--member="serviceAccount:$SERVICE_ACCOUNT_NAME@$PROJECT_ID.iam.gserviceaccount.com"
When setting roles in Terraform, you can grant roles with the google_organization_iam_member resource, as follows:
// Assuming:
// resource "google_service_account" "shisho_cloud" {
// project = var.project
// account_id = "shisho-cloud"
// description = "A service account that Shisho Cloud impersonates and use for listing up projects, resources, and their settings. Visit https://shisho.dev/docs/ja/g/getting-started/integrate-apps/googlecloud for further details."
// }
resource "google_organization_iam_member" "shisho_cloud_org_security" {
// org_id should come from `gcloud organizations list`
org_id = "1234567890"
role = "roles/iam.securityReviewer"
member = "serviceAccount:${google_service_account.shisho_cloud.email}"
}
resource "google_organization_iam_member" "shisho_cloud_org_bigquery" {
// org_id should come from `gcloud organizations list`
org_id = "1234567890"
role = "roles/bigquery.metadataViewer"
member = "serviceAccount:${google_service_account.shisho_cloud.email}"
}
resource "google_organization_iam_member" "shisho_cloud_org_policy" {
// org_id should come from `gcloud organizations list`
org_id = "1234567890"
role = "roles/orgpolicy.policyViewer"
member = "serviceAccount:${google_service_account.shisho_cloud.email}"
}
resource "google_organization_iam_member" "shisho_cloud_browser" {
// org_id should come from `gcloud organizations list`
org_id = "1234567890"
role = "roles/browser"
member = "serviceAccount:${google_service_account.shisho_cloud.email}"
}
resource "google_organization_iam_member" "shisho_cloud_access_approval" {
// org_id should come from `gcloud organizations list`
org_id = "1234567890"
role = "roles/accessapproval.viewer"
member = "serviceAccount:${google_service_account.shisho_cloud.email}"
}
resource "google_organization_iam_member" "shisho_cloud_firebase_auth" {
// org_id should come from `gcloud organizations list`
org_id = "1234567890"
role = "roles/firebaseauth.viewer"
member = "serviceAccount:${google_service_account.shisho_cloud.email}"
}
resource "google_organization_iam_member" "shisho_cloud_service_usage" {
// org_id should come from `gcloud organizations list`
org_id = "1234567890"
role = "roles/serviceusage.serviceUsageConsumer"
member = "serviceAccount:${google_service_account.shisho_cloud.email}"
}
resource "google_organization_iam_member" "shisho_cloud_compute_viewer" {
// org_id should come from `gcloud organizations list`
org_id = "1234567890"
role = "roles/compute.viewer"
member = "serviceAccount:${google_service_account.shisho_cloud.email}"
}
After opening the IAM & Admin console, click the project name (next to the Google Cloud logo) at the top of the screen. Then, you will see the following project, folder, and organization selector:

Then, if you select the "All" tab, you will be able to see the organization name (in the example image, flatt.tech) and folder names that group your company's Google Cloud projects.
If you want to inspect the entire organization with Shisho Cloud, click the organization name (in the example image, flatt.tech).

Then, if your Google Cloud account has sufficient privileges to configure organization settings (such as Google Workspace or Cloud Identity administrator roles), you will see a screen like the one below:

Then click the "Grant Access" button. Then, you will see a screen like the one below:

After entering the following in the displayed screen, press the "Save" button:
- New principals: The address of the service account you created (e.g.,
shisho-cloud@<project name>.iam.gserviceaccount.com; if you used Cloud Shell or gcloud CLI when "Creating a Service Account and Related Resources," the value displayed afterService Account Email:) - Role: All four of the following roles
roles/iam.securityReviewer(Security Reviewer)roles/bigquery.metadataViewer(BigQuery Metadata Viewer)roles/orgpolicy.policyViewer(Organization Policy Viewer)roles/browser(Browser)roles/accessapproval.viewer(Access Approval Viewer)roles/firebaseauth.viewer(Firebase Authentication Viewer)roles/serviceusage.serviceUsageConsumer(Service Usage Consumer)roles/compute.viewer(Compute Viewer)
Registering Information to Shisho Cloud
In the steps so far, you have completed setting up the service account that Shisho Cloud will use during the inspection, as well as the service account's access rights. Finally, click the "Settings" button on the "Google Cloud" card displayed on the "Gear icon ⚙ > Integrations" screen, and enter the necessary information by following the on-screen instructions. If you set up with the gcloud CLI (including using it on Cloud Shell), you will mainly need the values (1) - (4) output after the script execution.
When you have completed the input, the service account should appear on the setting page with a check mark, like the following:
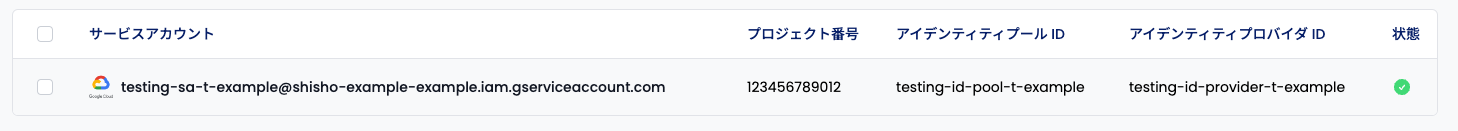
If you see this, the Google Cloud integration setup is complete. Shisho Cloud is now able to access your Google Cloud account!
Due to Google Cloud's caching specifications, Shisho Cloud may not be able to access Google Cloud for a few minutes after integration. If the configuration is not completed immediately, please wait up to 5 minutes.
If you are unable to successfully integrate Google Cloud by following the above steps, please feel free to contact the service provider (Flatt Security).
Reference: Technical Details of Google Cloud Integration
The setup procedure described above uses Google Cloud's Workload Identity Federation feature, along with service accounts. Workload Identity Federation is a framework for granting external identities the authority to act as service accounts on Google Cloud.
Shisho Cloud takes advantage of this framework to retrieve configuration settings for Google Cloud resources without a service account key. This is roughly equivalent to the mechanism of OIDC-based Google Cloud/Google Cloud integration that GitHub Actions has.
Functions and Concepts Setup
Of this framework, two functions/concepts are actually used to have Shisho Cloud perform security scans:
- Workload Identity Pool
- Workload Identity Provider
In the setup procedure described above, we first prepared a Workload Identity Pool. This is to associate external identities (external from Google's point of view, here the identity representing the workflow execution on Shisho Cloud) with principals within Google Cloud.
A Workload Identity Provider was then registered with the Workload Identity Pool. This is used to map and verify information (such as ID tokens) representing external identities with identities within the Workload Identity Pool. In the case of Shisho Cloud, since an ID token is issued for each workflow execution, the Workflow Identity Provider created is configured to associate that token with a principal on Google Cloud.
Flow of Access to the Google Cloud Environment
When Shisho Cloud actually tries to access Google Cloud, Shisho Cloud sends the ID token it issued to the Security Token Service API (STS) that Google Cloud has. The STS that received the ID token verifies the token.
One of the validations performed here is the verification of the JWT signature. The public key required for verification is provided at Shisho Cloud's JWKs endpoint, which is registered during the Workload Identity Federation configuration process.
The verification also verifies the information (claims) in the JWT payload. This is based on the mapping information and verification logic registered with the Workload Identity Pool Provider.
If the above verification is successful, the STS returns a short-lived access token to Google Cloud to Shisho Cloud. Shisho Cloud then passes this access token to the IAM API to request another access token to act as a service account. In the setup procedure described above, we granted the service account the Workload Identity User role, which is the setting to allow such requests.
Finally, Shisho Cloud obtains an access token with the authority to act as a service account.
In the setup procedure described above, we granted the service account roles such as roles/iam.securityReviewer, so Shisho Cloud is now able to read the configuration settings of Google Cloud resources.