AWS
Shisho Cloud と AWS を連携することで、AWS アカウントのセキュリティスキャンが実施できます。 この連携は以下の 2 ステップで行えます:
- 対象の AWS アカウントに Shisho Cloud が利用(assume)できる IAM ロールと、関連する ID プロバイダを作成する。
- 作成した IAM ロールの ARN を Shisho Cloud に登録する。
Shisho Cloud は IAM アクセスキーを必要とせず、その代わりに sts:AssumeRoleWithWebIdentity を用いた Web Identity Federation により、短命の認証情報を適宜発行しながら AWS にアクセスします。
これはおよそ GitHub Action が有する OIDC ベースの AWS/Google Cloud 連携の仕組み と同等の仕組みです。
IAM ロールの作成
以下のどれかの手順に従って、IAM ロールを作成してください:
一部のリソースに対する s3:GetObject アクションは、ご連携いただいた AWS アカウント内の S3 オブジェクトへのアクセスを許可しないように制限されています。したがって AWS アカウントを Shisho Cloud にご連携頂いても、Shisho Cloud がお客様が管理する S3 内のデータを読み取ることはありません。
逆に、ご連携いただいた AWS アカウント以外の一部の S3 オブジェクト(リソースが含まれるアカウント s3:ResourceAccount が、Shisho Cloud が利用するロールが存在するアカウントとは異なるようなオブジェクト)に対してのみ、読み取りアクセスが許可されています。これは Elastic Beanstalk の設定検査時に必要となるためです。AWS は Elastic Beanstalk の設定情報を、AWS が管理する別アカウント内の S3 バケット(arn:aws:s3:::elasticbeanstalk-env-resources-*/* 等)に内部的に格納しています。その上で、Elastic Beanstalk の一部の API の利用時には、API の呼び出し元が当該バケットに対する関連権限を持たなくてはなりません。実際、AWS が管理する IAM ポリシーである AWSElasticBeanstalkRoleCore は当該権限を含んでいることも確認できます。
- Terraform
- AWS CLI
- CloudFormation
変数 shisho_cloud_org_id の値をご自身の Shisho Cloud 組織の ID に変更した後、以下の Terraform 実装をご自身の Terraform プロジェクトに含め、 terraform apply を実行してください。
locals {
# Replace this with your Shisho Cloud org ID
shisho_cloud_org_id = "your-organization-id"
}
# The `aws_caller_identity` data is used to fetch the current AWS account ID.
data "aws_caller_identity" "shisho_cloud" {}
# Shisho Cloud connects to your AWS account via OIDC federation.
# The following `tls_certificate` resource will fetch the required certificate.
data "tls_certificate" "shisho_cloud_tokens_endpoint" {
url = "https://tokens.cloud.shisho.dev/.well-known/openid-configuration"
}
# The following `aws_iam_openid_connect_provider` resource will create the OIDC provider.
resource "aws_iam_openid_connect_provider" "shisho_cloud" {
url = "https://tokens.cloud.shisho.dev"
client_id_list = ["sts.amazonaws.com"]
thumbprint_list = data.tls_certificate.shisho_cloud_tokens_endpoint.certificates[*].sha1_fingerprint
}
# The following `aws_iam_role` resource will create the IAM role that Shisho Cloud will assume.
resource "aws_iam_role" "shisho_cloud_audit" {
name = "ShishoCloudSecurityAudit"
description = "IAM role for Shisho Cloud"
assume_role_policy = jsonencode({
"Version" : "2012-10-17",
"Statement" : [
{
"Effect" : "Allow",
"Principal" : {
"Federated" : aws_iam_openid_connect_provider.shisho_cloud.arn,
},
"Action" : "sts:AssumeRoleWithWebIdentity",
"Condition" : {
"StringLike" : {
# Allow AssumeRole for any job in the Shisho Cloud org
"tokens.cloud.shisho.dev:sub" : "job:${local.shisho_cloud_org_id}:*"
},
"StringEquals" : {
"tokens.cloud.shisho.dev:aud" : "sts.amazonaws.com"
}
}
}
]
})
}
resource "aws_iam_role_policy" "shisho_cloud_audit" {
role = aws_iam_role.shisho_cloud_audit.id
name = "ResourceAccessPolicy"
policy = jsonencode({
"Version" : "2012-10-17",
"Statement" : [
{
"Effect" : "Allow",
"Action" : [
"access-analyzer:ListAnalyzers",
"account:GetAlternateContact",
"acm:DescribeCertificate",
"acm:ListCertificates",
"apigateway:GET",
"autoscaling:DescribeAutoScalingGroups",
"autoscaling:DescribeLaunchConfigurations",
"autoscaling:DescribeNotificationConfigurations",
"cloudformation:DescribeStacks",
"cloudformation:GetStackPolicy",
"cloudformation:GetTemplate",
"cloudformation:ListStacks",
"cloudformation:ListStackResources",
"cloudfront:ListDistributions",
"cloudfront:GetDistributionConfig",
"cloudfront:GetResponseHeadersPolicy",
"cloudfront:GetCachePolicy",
"cloudfront:GetOriginRequestPolicy",
"cloudtrail:DescribeTrails",
"cloudtrail:GetEventSelectors",
"cloudtrail:GetTrailStatus",
"cloudwatch:DescribeAlarms",
"codebuild:ListProjects",
"codebuild:ListSourceCredentials",
"codebuild:BatchGetProjects",
"cognito-identity:DescribeIdentityPool",
"cognito-identity:ListIdentityPools",
"cognito-identity:GetIdentityPoolRoles",
"cognito-identity:GetPrincipalTagAttributeMap",
"cognito-idp:ListUserPoolClients",
"cognito-idp:DescribeUserPoolClient",
"cognito-idp:GetGroup",
"cognito-idp:ListGroups",
"cognito-idp:DescribeUserPoolDomain",
"cognito-idp:DescribeRiskConfiguration",
"cognito-idp:GetUserPoolMfaConfig",
"cognito-idp:ListIdentityProviders",
"cognito-idp:DescribeIdentityProvider",
"cognito-idp:GetIdentityProviderByIdentifier",
"cognito-idp:DescribeResourceServer",
"cognito-idp:ListResourceServers",
"cognito-idp:DescribeRiskConfiguration",
"cognito-idp:GetUICustomization",
"cognito-idp:GetSigningCertificate",
"cognito-idp:GetLogDeliveryConfiguration",
"cognito-idp:DescribeUserPool",
"cognito-idp:ListUserPools",
"cognito-idp:GetWebACLForResource",
"config:DescribeConfigRules",
"config:DescribeConfigurationRecorderStatus",
"config:DescribeConfigurationRecorders",
"directconnect:DescribeConnections",
"dms:DescribeReplicationInstances",
"dynamodb:DescribeContinuousBackups",
"dynamodb:DescribeTable",
"dynamodb:DescribeExport",
"dynamodb:DescribeKinesisStreamingDestination",
"dynamodb:ListBackups",
"dynamodb:ListTables",
"dynamodb:ListTagsOfResource",
"dynamodb:ListExports",
"ec2:DescribeAddresses",
"ec2:DescribeCustomerGateways",
"ec2:DescribeFlowLogs",
"ec2:DescribeImages",
"ec2:DescribeInstanceAttribute",
"ec2:DescribeInstances",
"ec2:DescribeLaunchTemplates",
"ec2:DescribeLaunchTemplateVersions",
"ec2:DescribeNetworkAcls",
"ec2:DescribeNetworkInterfaceAttribute",
"ec2:DescribeNetworkInterfaces",
"ec2:DescribeRegions",
"ec2:DescribeRouteTables",
"ec2:DescribeSecurityGroups",
"ec2:DescribeSecurityGroupRules",
"ec2:DescribeSnapshotAttribute",
"ec2:DescribeSnapshots",
"ec2:DescribeSubnets",
"ec2:DescribeTransitGateways",
"ec2:DescribeVolumes",
"ec2:DescribeIamInstanceProfileAssociations",
"ec2:DescribeVpcEndpoints",
"ec2:DescribeVpcPeeringConnections",
"ec2:DescribeVpcs",
"ec2:DescribeVpnConnections",
"ec2:DescribeVpnGateways",
"ec2:GetEbsEncryptionByDefault",
"ecr:DescribeImages",
"ecr:DescribeRepositories",
"ecr:GetLifecyclePolicy",
"ecr:GetRepositoryPolicy",
"ecr:ListImages",
"ecs:ListClusters",
"ecs:DescribeClusters",
"ecs:ListServices",
"ecs:DescribeServices",
"ecs:ListTasks",
"ecs:DescribeTasks",
"ecs:ListTaskDefinitions",
"ecs:DescribeTaskDefinition",
"ecs:ListAccountSettings",
"eks:DescribeCluster",
"eks:ListClusters",
"eks:ListNodegroups",
"eks:DescribeNodegroup",
"eks:ListFargateProfiles",
"eks:DescribeFargateProfile",
"elasticbeanstalk:DescribeConfigurationSettings",
"elasticbeanstalk:DescribeEnvironmentResources",
"elasticbeanstalk:DescribeEnvironments",
"elasticache:DescribeCacheClusters",
"elasticache:DescribeCacheParameterGroups",
"elasticache:DescribeCacheParameters",
"elasticache:DescribeCacheSecurityGroups",
"elasticache:DescribeCacheSubnetGroups",
"elasticache:DescribeReplicationGroups",
"elasticache:DescribeUsers",
"elasticfilesystem:DescribeAccessPoints",
"elasticfilesystem:DescribeFileSystems",
"elasticfilesystem:DescribeMountTargetSecurityGroups",
"elasticfilesystem:DescribeMountTargets",
"elasticfilesystem:DescribeTags",
"elasticfilesystem:DescribeBackupPolicy",
"elasticfilesystem:DescribeFileSystemPolicy",
"elasticloadbalancing:DescribeListeners",
"elasticloadbalancing:DescribeLoadBalancerAttributes",
"elasticloadbalancing:DescribeLoadBalancerPolicies",
"elasticloadbalancing:DescribeLoadBalancers",
"elasticloadbalancing:DescribeSSLPolicies",
"elasticloadbalancing:DescribeTags",
"elasticloadbalancing:DescribeTargetGroups",
"elasticloadbalancing:DescribeTargetHealth",
"elasticloadbalancing:DescribeInstanceHealth",
"elasticmapreduce:DescribeCluster",
"elasticmapreduce:ListClusters",
"es:ListDomainNames",
"es:DescribeElasticsearchDomains",
"es:DescribeDomains",
"dax:DescribeClusters",
"dax:DescribeSubnetGroups",
"events:ListEndpoints",
"events:ListEventBuses",
"events:DescribeEventBus",
"guardduty:GetDetector",
"guardduty:ListDetectors",
"iam:GenerateCredentialReport",
"iam:GetAccountPasswordPolicy",
"iam:GetCredentialReport",
"iam:GetGroup",
"iam:GetGroupPolicy",
"iam:GetLoginProfile",
"iam:GetPolicy",
"iam:GetPolicyVersion",
"iam:GetRole",
"iam:GetRolePolicy",
"iam:GetUserPolicy",
"iam:GetAccountSummary",
"iam:GetAccessKeyLastUsed",
"iam:GetAccountAuthorizationDetails",
"iam:ListAccessKeys",
"iam:ListAttachedRolePolicies",
"iam:ListAttachedUserPolicies",
"iam:ListEntitiesForPolicy",
"iam:ListGroupPolicies",
"iam:ListGroups",
"iam:ListGroupsForUser",
"iam:ListInstanceProfilesForRole",
"iam:ListInstanceProfiles",
"iam:GetInstanceProfile",
"iam:ListMFADevices",
"iam:ListPolicies",
"iam:ListRolePolicies",
"iam:ListRoleTags",
"iam:ListRoles",
"iam:ListUserPolicies",
"iam:ListUserTags",
"iam:ListUsers",
"iam:ListVirtualMFADevices",
"iam:ListServerCertificates",
"iam:ListAccountAliases",
"kinesis:ListStreams",
"kinesis:DescribeStream",
"kms:DescribeKey",
"kms:GetKeyPolicy",
"kms:GetKeyRotationStatus",
"kms:ListAliases",
"kms:ListGrants",
"kms:ListKeys",
"network-firewall:ListFirewallPolicies",
"network-firewall:ListFirewalls",
"network-firewall:ListRuleGroups",
"network-firewall:DescribeFirewall",
"network-firewall:DescribeFirewallPolicy",
"network-firewall:DescribeRuleGroup",
"lambda:GetFunctionConfiguration",
"lambda:GetFunctionEventInvokeConfig",
"lambda:GetPolicy",
"lambda:ListFunctions",
"lambda:ListEventSourceMappings",
"logs:DescribeLogGroups",
"logs:DescribeMetricFilters",
"rds:DescribeDBClusterSnapshotAttributes",
"rds:DescribeDBClusterSnapshots",
"rds:DescribeDBClusters",
"rds:DescribeDBInstances",
"rds:DescribeDBParameterGroups",
"rds:DescribeDBParameters",
"rds:DescribeDBSecurityGroups",
"rds:DescribeDBSnapshotAttributes",
"rds:DescribeDBSnapshots",
"rds:DescribeDBSubnetGroups",
"rds:DescribeEventSubscriptions",
"rds:ListTagsForResource",
"redshift:DescribeClusterParameterGroups",
"redshift:DescribeClusterParameters",
"redshift:DescribeClusterSecurityGroups",
"redshift:DescribeClusterSubnetGroups",
"redshift:DescribeClusters",
"redshift:DescribeLoggingStatus",
"route53:GetHostedZone",
"route53:ListHostedZones",
"route53:ListResourceRecordSets",
"route53:ListTagsForResource",
"route53domains:ListDomains",
"s3:GetAccountPublicAccessBlock",
"s3:GetBucketAcl",
"s3:GetBucketLocation",
"s3:GetBucketLogging",
"s3:GetBucketNotification",
"s3:GetBucketObjectLockConfiguration",
"s3:GetBucketOwnershipControls",
"s3:GetBucketPolicy",
"s3:GetBucketPublicAccessBlock",
"s3:GetBucketTagging",
"s3:GetBucketVersioning",
"s3:GetBucketWebsite",
"s3:GetEncryptionConfiguration",
"s3:GetLifecycleConfiguration",
"s3:GetReplicationConfiguration",
"s3:ListAllMyBuckets",
"sagemaker:ListNotebookInstances",
"sagemaker:DescribeNotebookInstance",
"sagemaker:DescribeNotebookInstanceLifecycleConfig",
"secretsmanager:ListSecrets",
"secretsmanager:DescribeSecret",
"securityhub:DescribeHub",
"ses:GetIdentityDkimAttributes",
"ses:GetIdentityPolicies",
"ses:ListIdentities",
"ses:ListIdentityPolicies",
"states:ListStateMachines",
"states:DescribeStateMachine",
"ssm:DescribeParameters",
"ssm:GetParameters",
"ssm:ListComplianceItems",
"ssm:ListDocuments",
"ssm:DescribeDocument",
"ssm:DescribeDocumentPermission",
"ssm:DescribeInstanceInformation",
"sns:GetTopicAttributes",
"sns:GetSubscriptionAttributes",
"sns:ListSubscriptions",
"sns:ListSubscriptionsByTopic",
"sns:ListTopics",
"sqs:GetQueueAttributes",
"sqs:GetQueueUrl",
"sqs:ListQueues",
"waf:ListActivatedRulesInRuleGroup",
"waf:ListRuleGroups",
"waf:ListRules",
"waf:ListWebACLs",
"waf:GetLoggingConfiguration",
"waf:GetRateBasedRule",
"waf:GetRuleGroup",
"waf:GetRule",
"waf:GetWebACL",
"wafv2:ListWebACLs",
"wafv2:GetWebACL",
"wafv2:GetWebACLForResource",
"wafv2:GetLoggingConfiguration",
"wafv2:ListIPSets",
"wafv2:GetIPSet",
"wafv2:ListRuleGroups",
"wafv2:GetRuleGroup",
"waf-regional:ListActivatedRulesInRuleGroup",
"waf-regional:ListWebACLs",
"waf-regional:ListRuleGroups",
"waf-regional:ListRules",
"waf-regional:GetLoggingConfiguration",
"waf-regional:GetRateBasedRule",
"waf-regional:GetRuleGroup",
"waf-regional:GetRule",
"waf-regional:GetWebACL",
"tag:Get*"
],
"Resource" : "*"
},
{
"Effect" : "Allow",
"Action" : ["s3:GetObject"],
"Resource" : [
"arn:aws:s3:::elasticbeanstalk-env-resources-*/*"
],
"Condition" : {
"StringNotLike" : {
"s3:ResourceAccount" : "${data.aws_caller_identity.shisho_cloud.account_id}"
}
}
}
]
})
}
冒頭の SHISHO_ORG_IDの値(必須)、AWS_CLI_OPTS の値(任意)を適宜変更した後、以下のスクリプトを実行することで、必要なリソース(ID プロバイダ・IAM ロール)が作成されます:
#!/bin/bash
set -eu
# Input values
############
# Any additional values for your AWS CLI
# Example: --profile your-profile-name
AWS_CLI_OPTS=""
# Your Shisho Cloud organization ID
SHISHO_ORG_ID="your-organization-id"
# AWS Account ID to be reviewed by Shisho Cloud
AWS_ACCOUNT_ID="$(aws sts get-caller-identity $AWS_CLI_OPTS --query "Account" --output "text")"
# Constants
############
TOKEN_ENDPOINT_URL="https://tokens.cloud.shisho.dev"
TOKEN_ENDPOINT_HOST="tokens.cloud.shisho.dev"
OIDC_THUMBPRINT="9e99a48a9960b14926bb7f3b02e22da2b0ab7280"
# The name of an IAM role to create for Shisho Cloud
ROLE_NAME="ShishoCloudSecurityAudit"
# Setting up all resouces
############
echo "[*] Create an OIDC provider: $TOKEN_ENDPOINT_URL"
aws iam create-open-id-connect-provider \
$AWS_CLI_OPTS \
--url "$TOKEN_ENDPOINT_URL" \
--client-id-list "sts.amazonaws.com" \
--thumbprint-list "$OIDC_THUMBPRINT"
echo "[*] Create a role assumable by the OIDC provider: $ROLE_NAME"
PROVIDER_ARN="arn:aws:iam::${AWS_ACCOUNT_ID}:oidc-provider/${TOKEN_ENDPOINT_HOST}"
ASSUME_ROLE_POLICY_DOCUMENT="$(cat <<EOF
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "$PROVIDER_ARN"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringLike": {
"${TOKEN_ENDPOINT_HOST}:sub": "job:${SHISHO_ORG_ID}:*"
},
"StringEquals": {
"${TOKEN_ENDPOINT_HOST}:aud": "sts.amazonaws.com"
}
}
}
]
}
EOF
)"
aws iam create-role \
$AWS_CLI_OPTS \
--role-name "$ROLE_NAME" \
--assume-role-policy-document "$ASSUME_ROLE_POLICY_DOCUMENT"
# Give the role permissions to access AWS resources according to $POLICY_DOCUMENT
echo "[*] Give the role permissions to access AWS resources"
POLICY_DOCUMENT="$(cat <<EOF
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"access-analyzer:ListAnalyzers",
"account:GetAlternateContact",
"acm:DescribeCertificate",
"acm:ListCertificates",
"apigateway:GET",
"autoscaling:DescribeAutoScalingGroups",
"autoscaling:DescribeLaunchConfigurations",
"autoscaling:DescribeNotificationConfigurations",
"cloudformation:DescribeStacks",
"cloudformation:GetStackPolicy",
"cloudformation:GetTemplate",
"cloudformation:ListStackResources",
"cloudformation:ListStacks",
"cloudfront:GetCachePolicy",
"cloudfront:GetDistributionConfig",
"cloudfront:GetOriginRequestPolicy",
"cloudfront:GetResponseHeadersPolicy",
"cloudfront:ListDistributions",
"cloudtrail:DescribeTrails",
"cloudtrail:GetEventSelectors",
"cloudtrail:GetTrailStatus",
"cloudwatch:DescribeAlarms",
"codebuild:BatchGetProjects",
"codebuild:ListProjects",
"codebuild:ListSourceCredentials",
"cognito-identity:DescribeIdentityPool",
"cognito-identity:GetIdentityPoolRoles",
"cognito-identity:GetPrincipalTagAttributeMap",
"cognito-identity:ListIdentityPools",
"cognito-idp:DescribeIdentityProvider",
"cognito-idp:DescribeResourceServer",
"cognito-idp:DescribeRiskConfiguration",
"cognito-idp:DescribeUserPool",
"cognito-idp:DescribeUserPoolClient",
"cognito-idp:DescribeUserPoolDomain",
"cognito-idp:GetGroup",
"cognito-idp:GetIdentityProviderByIdentifier",
"cognito-idp:GetLogDeliveryConfiguration",
"cognito-idp:GetSigningCertificate",
"cognito-idp:GetUICustomization",
"cognito-idp:GetUserPoolMfaConfig",
"cognito-idp:GetWebACLForResource",
"cognito-idp:ListGroups",
"cognito-idp:ListIdentityProviders",
"cognito-idp:ListResourceServers",
"cognito-idp:ListUserPoolClients",
"cognito-idp:ListUserPools",
"config:DescribeConfigRules",
"config:DescribeConfigurationRecorderStatus",
"config:DescribeConfigurationRecorders",
"dax:DescribeClusters",
"dax:DescribeSubnetGroups",
"directconnect:DescribeConnections",
"dms:DescribeReplicationInstances",
"dynamodb:DescribeContinuousBackups",
"dynamodb:DescribeExport",
"dynamodb:DescribeKinesisStreamingDestination",
"dynamodb:DescribeTable",
"dynamodb:ListBackups",
"dynamodb:ListExports",
"dynamodb:ListTables",
"dynamodb:ListTagsOfResource",
"ec2:DescribeAddresses",
"ec2:DescribeCustomerGateways",
"ec2:DescribeFlowLogs",
"ec2:DescribeImages",
"ec2:DescribeInstanceAttribute",
"ec2:DescribeInstances",
"ec2:DescribeLaunchTemplateVersions",
"ec2:DescribeLaunchTemplates",
"ec2:DescribeNetworkAcls",
"ec2:DescribeNetworkInterfaceAttribute",
"ec2:DescribeNetworkInterfaces",
"ec2:DescribeRegions",
"ec2:DescribeRouteTables",
"ec2:DescribeSecurityGroupRules",
"ec2:DescribeSecurityGroups",
"ec2:DescribeSnapshotAttribute",
"ec2:DescribeSnapshots",
"ec2:DescribeSubnets",
"ec2:DescribeTransitGateways",
"ec2:DescribeVolumes",
"ec2:DescribeIamInstanceProfileAssociations",
"ec2:DescribeVpcEndpoints",
"ec2:DescribeVpcPeeringConnections",
"ec2:DescribeVpcs",
"ec2:DescribeVpnConnections",
"ec2:DescribeVpnGateways",
"ec2:GetEbsEncryptionByDefault",
"ecr:DescribeImages",
"ecr:DescribeRepositories",
"ecr:GetLifecyclePolicy",
"ecr:GetRepositoryPolicy",
"ecr:ListImages",
"ecs:DescribeClusters",
"ecs:DescribeServices",
"ecs:DescribeTaskDefinition",
"ecs:DescribeTasks",
"ecs:ListAccountSettings",
"ecs:ListClusters",
"ecs:ListServices",
"ecs:ListTaskDefinitions",
"ecs:ListTasks",
"eks:DescribeCluster",
"eks:DescribeFargateProfile",
"eks:DescribeNodegroup",
"eks:ListClusters",
"eks:ListFargateProfiles",
"eks:ListNodegroups",
"elasticache:DescribeCacheClusters",
"elasticache:DescribeCacheParameterGroups",
"elasticache:DescribeCacheParameters",
"elasticache:DescribeCacheSecurityGroups",
"elasticache:DescribeCacheSubnetGroups",
"elasticache:DescribeReplicationGroups",
"elasticache:DescribeUsers",
"elasticbeanstalk:DescribeConfigurationSettings",
"elasticbeanstalk:DescribeEnvironmentResources",
"elasticbeanstalk:DescribeEnvironments",
"elasticfilesystem:DescribeAccessPoints",
"elasticfilesystem:DescribeBackupPolicy",
"elasticfilesystem:DescribeFileSystemPolicy",
"elasticfilesystem:DescribeFileSystems",
"elasticfilesystem:DescribeMountTargetSecurityGroups",
"elasticfilesystem:DescribeMountTargets",
"elasticfilesystem:DescribeTags",
"elasticloadbalancing:DescribeInstanceHealth",
"elasticloadbalancing:DescribeListeners",
"elasticloadbalancing:DescribeLoadBalancerAttributes",
"elasticloadbalancing:DescribeLoadBalancerPolicies",
"elasticloadbalancing:DescribeLoadBalancers",
"elasticloadbalancing:DescribeSSLPolicies",
"elasticloadbalancing:DescribeTags",
"elasticloadbalancing:DescribeTargetGroups",
"elasticloadbalancing:DescribeTargetHealth",
"elasticmapreduce:DescribeCluster",
"elasticmapreduce:ListClusters",
"es:DescribeDomains",
"es:DescribeElasticsearchDomains",
"es:ListDomainNames",
"events:DescribeEventBus",
"events:ListEndpoints",
"events:ListEventBuses",
"guardduty:GetDetector",
"guardduty:ListDetectors",
"iam:GenerateCredentialReport",
"iam:GetAccessKeyLastUsed",
"iam:GetAccountAuthorizationDetails",
"iam:GetAccountPasswordPolicy",
"iam:GetAccountSummary",
"iam:GetCredentialReport",
"iam:GetGroup",
"iam:GetGroupPolicy",
"iam:GetLoginProfile",
"iam:GetPolicy",
"iam:GetPolicyVersion",
"iam:GetRole",
"iam:GetRolePolicy",
"iam:GetUserPolicy",
"iam:ListAccessKeys",
"iam:ListAccountAliases",
"iam:ListAttachedRolePolicies",
"iam:ListAttachedUserPolicies",
"iam:ListEntitiesForPolicy",
"iam:ListGroupPolicies",
"iam:ListGroups",
"iam:ListGroupsForUser",
"iam:ListInstanceProfilesForRole",
"iam:ListInstanceProfiles",
"iam:GetInstanceProfile",
"iam:ListMFADevices",
"iam:ListPolicies",
"iam:ListRolePolicies",
"iam:ListRoleTags",
"iam:ListRoles",
"iam:ListServerCertificates",
"iam:ListUserPolicies",
"iam:ListUserTags",
"iam:ListUsers",
"iam:ListVirtualMFADevices",
"kinesis:DescribeStream",
"kinesis:ListStreams",
"kms:DescribeKey",
"kms:GetKeyPolicy",
"kms:GetKeyRotationStatus",
"kms:ListAliases",
"kms:ListGrants",
"kms:ListKeys",
"lambda:GetFunctionConfiguration",
"lambda:GetFunctionEventInvokeConfig",
"lambda:GetPolicy",
"lambda:ListEventSourceMappings",
"lambda:ListFunctions",
"logs:DescribeLogGroups",
"logs:DescribeMetricFilters",
"network-firewall:DescribeFirewall",
"network-firewall:DescribeFirewallPolicy",
"network-firewall:DescribeRuleGroup",
"network-firewall:ListFirewallPolicies",
"network-firewall:ListFirewalls",
"network-firewall:ListRuleGroups",
"rds:DescribeDBClusterSnapshotAttributes",
"rds:DescribeDBClusterSnapshots",
"rds:DescribeDBClusters",
"rds:DescribeDBInstances",
"rds:DescribeDBParameterGroups",
"rds:DescribeDBParameters",
"rds:DescribeDBSecurityGroups",
"rds:DescribeDBSnapshotAttributes",
"rds:DescribeDBSnapshots",
"rds:DescribeDBSubnetGroups",
"rds:DescribeEventSubscriptions",
"rds:ListTagsForResource",
"redshift:DescribeClusterParameterGroups",
"redshift:DescribeClusterParameters",
"redshift:DescribeClusterSecurityGroups",
"redshift:DescribeClusterSubnetGroups",
"redshift:DescribeClusters",
"redshift:DescribeLoggingStatus",
"route53:GetHostedZone",
"route53:ListHostedZones",
"route53:ListResourceRecordSets",
"route53:ListTagsForResource",
"route53domains:ListDomains",
"s3:GetAccountPublicAccessBlock",
"s3:GetBucketAcl",
"s3:GetBucketLocation",
"s3:GetBucketLogging",
"s3:GetBucketNotification",
"s3:GetBucketObjectLockConfiguration",
"s3:GetBucketOwnershipControls",
"s3:GetBucketPolicy",
"s3:GetBucketPublicAccessBlock",
"s3:GetBucketTagging",
"s3:GetBucketVersioning",
"s3:GetBucketWebsite",
"s3:GetEncryptionConfiguration",
"s3:GetLifecycleConfiguration",
"s3:GetReplicationConfiguration",
"s3:ListAllMyBuckets",
"sagemaker:DescribeNotebookInstance",
"sagemaker:DescribeNotebookInstanceLifecycleConfig",
"sagemaker:ListNotebookInstances",
"secretsmanager:DescribeSecret",
"secretsmanager:ListSecrets",
"securityhub:DescribeHub",
"ses:GetIdentityDkimAttributes",
"ses:GetIdentityPolicies",
"ses:ListIdentities",
"ses:ListIdentityPolicies",
"sns:GetSubscriptionAttributes",
"sns:GetTopicAttributes",
"sns:ListSubscriptions",
"sns:ListSubscriptionsByTopic",
"sns:ListTopics",
"sqs:GetQueueAttributes",
"sqs:GetQueueUrl",
"sqs:ListQueues",
"ssm:DescribeDocument",
"ssm:DescribeDocumentPermission",
"ssm:DescribeInstanceInformation",
"ssm:DescribeParameters",
"ssm:GetParameters",
"ssm:ListComplianceItems",
"ssm:ListDocuments",
"states:DescribeStateMachine",
"states:ListStateMachines",
"waf-regional:GetLoggingConfiguration",
"waf-regional:GetRateBasedRule",
"waf-regional:GetRule",
"waf-regional:GetRuleGroup",
"waf-regional:GetWebACL",
"waf-regional:ListActivatedRulesInRuleGroup",
"waf-regional:ListRuleGroups",
"waf-regional:ListRules",
"waf-regional:ListWebACLs",
"waf:GetLoggingConfiguration",
"waf:GetRateBasedRule",
"waf:GetRule",
"waf:GetRuleGroup",
"waf:GetWebACL",
"waf:ListActivatedRulesInRuleGroup",
"waf:ListRuleGroups",
"waf:ListRules",
"waf:ListWebACLs",
"wafv2:GetLoggingConfiguration",
"wafv2:GetWebACL",
"wafv2:GetWebACLForResource",
"wafv2:ListWebACLs",
"wafv2:ListIPSets",
"wafv2:GetIPSet",
"wafv2:ListRuleGroups",
"wafv2:GetRuleGroup",
"tag:Get*"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [ "s3:GetObject" ],
"Resource": [
"arn:aws:s3:::elasticbeanstalk-env-resources-*/*"
],
"Condition": {
"StringNotLike": {
"s3:ResourceAccount": "$AWS_ACCOUNT_ID"
}
}
}
]
}
EOF
)"
aws iam put-role-policy \
$AWS_CLI_OPTS \
--role-name "$ROLE_NAME" \
--policy-name "ResourceAccessPolicy" \
--policy-document "$POLICY_DOCUMENT"
# Postprocessing
############
echo "[*] Visit https://cloud.shisho.dev/${SHISHO_ORG_ID}/settings/integrations/aws and add a federation with:"
echo "- Role ARN: arn:aws:iam::${AWS_ACCOUNT_ID}:role/${ROLE_NAME}"
以下の CloudFormation テンプレートを利用して IAM ロールを作成してください。
なお、テンプレートの利用時には、パラメータ ShishoCloudOrgId にはご自身が作成した Shisho Cloud 組織の ID を指定してください。
AWSTemplateFormatVersion: "2010-09-09"
Parameters:
ShishoCloudOrgId:
Type: String
Description: "Your Shisho Cloud org ID"
Resources:
ShishoCloudAuditRole:
Type: "AWS::IAM::Role"
Properties:
RoleName: "ShishoCloudSecurityAuditByCloudFormationTemplate"
Description: "IAM role for Shisho Cloud"
AssumeRolePolicyDocument:
Version: "2012-10-17"
Statement:
- Effect: "Allow"
Principal:
Federated: !Sub "arn:${AWS::Partition}:iam::${AWS::AccountId}:oidc-provider/tokens.cloud.shisho.dev"
Action: "sts:AssumeRoleWithWebIdentity"
Condition:
StringLike:
"tokens.cloud.shisho.dev:sub": !Sub "job:${ShishoCloudOrgId}:*"
StringEquals:
"tokens.cloud.shisho.dev:aud": "sts.amazonaws.com"
Policies:
- PolicyName: "ResourceAccessPolicy"
PolicyDocument:
Version: "2012-10-17"
Statement:
- Effect: "Allow"
Action:
- "access-analyzer:ListAnalyzers"
- "account:GetAlternateContact"
- "acm:DescribeCertificate"
- "acm:ListCertificates"
- "apigateway:GET"
- "autoscaling:DescribeAutoScalingGroups"
- "autoscaling:DescribeLaunchConfigurations"
- "autoscaling:DescribeNotificationConfigurations"
- "cloudformation:DescribeStacks"
- "cloudformation:GetStackPolicy"
- "cloudformation:GetTemplate"
- "cloudformation:ListStacks"
- "cloudformation:ListStackResources"
- "cloudfront:ListDistributions"
- "cloudfront:GetDistributionConfig"
- "cloudfront:GetResponseHeadersPolicy"
- "cloudfront:GetCachePolicy"
- "cloudfront:GetOriginRequestPolicy"
- "cloudtrail:DescribeTrails"
- "cloudtrail:GetEventSelectors"
- "cloudtrail:GetTrailStatus"
- "cloudwatch:DescribeAlarms"
- "codebuild:ListProjects"
- "codebuild:ListSourceCredentials"
- "codebuild:BatchGetProjects"
- "cognito-identity:DescribeIdentityPool"
- "cognito-identity:ListIdentityPools"
- "cognito-identity:GetIdentityPoolRoles"
- "cognito-identity:GetPrincipalTagAttributeMap"
- "cognito-idp:ListUserPoolClients"
- "cognito-idp:DescribeUserPoolClient"
- "cognito-idp:GetGroup"
- "cognito-idp:ListGroups"
- "cognito-idp:DescribeUserPoolDomain"
- "cognito-idp:DescribeRiskConfiguration"
- "cognito-idp:GetUserPoolMfaConfig"
- "cognito-idp:ListIdentityProviders"
- "cognito-idp:DescribeIdentityProvider"
- "cognito-idp:GetIdentityProviderByIdentifier"
- "cognito-idp:DescribeResourceServer"
- "cognito-idp:ListResourceServers"
- "cognito-idp:DescribeRiskConfiguration"
- "cognito-idp:GetUICustomization"
- "cognito-idp:GetSigningCertificate"
- "cognito-idp:GetLogDeliveryConfiguration"
- "cognito-idp:DescribeUserPool"
- "cognito-idp:ListUserPools"
- "cognito-idp:GetWebACLForResource"
- "config:DescribeConfigRules"
- "config:DescribeConfigurationRecorderStatus"
- "config:DescribeConfigurationRecorders"
- "directconnect:DescribeConnections"
- "dms:DescribeReplicationInstances"
- "dynamodb:DescribeContinuousBackups"
- "dynamodb:DescribeTable"
- "dynamodb:DescribeExport"
- "dynamodb:DescribeKinesisStreamingDestination"
- "dynamodb:ListBackups"
- "dynamodb:ListTables"
- "dynamodb:ListTagsOfResource"
- "dynamodb:ListExports"
- "ec2:DescribeAddresses"
- "ec2:DescribeCustomerGateways"
- "ec2:DescribeFlowLogs"
- "ec2:DescribeImages"
- "ec2:DescribeInstanceAttribute"
- "ec2:DescribeInstances"
- "ec2:DescribeLaunchTemplates"
- "ec2:DescribeLaunchTemplateVersions"
- "ec2:DescribeNetworkAcls"
- "ec2:DescribeNetworkInterfaceAttribute"
- "ec2:DescribeNetworkInterfaces"
- "ec2:DescribeRegions"
- "ec2:DescribeRouteTables"
- "ec2:DescribeSecurityGroups"
- "ec2:DescribeSecurityGroupRules"
- "ec2:DescribeSnapshotAttribute"
- "ec2:DescribeSnapshots"
- "ec2:DescribeSubnets"
- "ec2:DescribeTransitGateways"
- "ec2:DescribeVolumes"
- "ec2:DescribeIamInstanceProfileAssociations"
- "ec2:DescribeVpcEndpoints"
- "ec2:DescribeVpcPeeringConnections"
- "ec2:DescribeVpcs"
- "ec2:DescribeVpnConnections"
- "ec2:DescribeVpnGateways"
- "ec2:GetEbsEncryptionByDefault"
- "ecr:DescribeImages"
- "ecr:DescribeRepositories"
- "ecr:GetLifecyclePolicy"
- "ecr:GetRepositoryPolicy"
- "ecr:ListImages"
- "ecs:ListClusters"
- "ecs:DescribeClusters"
- "ecs:ListServices"
- "ecs:DescribeServices"
- "ecs:ListTasks"
- "ecs:DescribeTasks"
- "ecs:ListTaskDefinitions"
- "ecs:DescribeTaskDefinition"
- "ecs:ListAccountSettings"
- "eks:DescribeCluster"
- "eks:ListClusters"
- "eks:ListNodegroups"
- "eks:DescribeNodegroup"
- "eks:ListFargateProfiles"
- "eks:DescribeFargateProfile"
- "elasticbeanstalk:DescribeConfigurationSettings"
- "elasticbeanstalk:DescribeEnvironmentResources"
- "elasticbeanstalk:DescribeEnvironments"
- "elasticache:DescribeCacheClusters"
- "elasticache:DescribeCacheParameterGroups"
- "elasticache:DescribeCacheParameters"
- "elasticache:DescribeCacheSecurityGroups"
- "elasticache:DescribeCacheSubnetGroups"
- "elasticache:DescribeReplicationGroups"
- "elasticache:DescribeUsers"
- "elasticfilesystem:DescribeAccessPoints"
- "elasticfilesystem:DescribeFileSystems"
- "elasticfilesystem:DescribeMountTargetSecurityGroups"
- "elasticfilesystem:DescribeMountTargets"
- "elasticfilesystem:DescribeTags"
- "elasticfilesystem:DescribeBackupPolicy"
- "elasticfilesystem:DescribeFileSystemPolicy"
- "elasticloadbalancing:DescribeListeners"
- "elasticloadbalancing:DescribeLoadBalancerAttributes"
- "elasticloadbalancing:DescribeLoadBalancerPolicies"
- "elasticloadbalancing:DescribeLoadBalancers"
- "elasticloadbalancing:DescribeSSLPolicies"
- "elasticloadbalancing:DescribeTags"
- "elasticloadbalancing:DescribeTargetGroups"
- "elasticloadbalancing:DescribeTargetHealth"
- "elasticloadbalancing:DescribeInstanceHealth"
- "elasticmapreduce:DescribeCluster"
- "elasticmapreduce:ListClusters"
- "es:ListDomainNames"
- "es:DescribeElasticsearchDomains"
- "es:DescribeDomains"
- "dax:DescribeClusters"
- "dax:DescribeSubnetGroups"
- "events:ListEndpoints"
- "events:ListEventBuses"
- "events:DescribeEventBus"
- "guardduty:GetDetector"
- "guardduty:ListDetectors"
- "iam:GenerateCredentialReport"
- "iam:GetAccountPasswordPolicy"
- "iam:GetCredentialReport"
- "iam:GetGroup"
- "iam:GetGroupPolicy"
- "iam:GetLoginProfile"
- "iam:GetPolicy"
- "iam:GetPolicyVersion"
- "iam:GetRole"
- "iam:GetRolePolicy"
- "iam:GetUserPolicy"
- "iam:GetAccountSummary"
- "iam:GetAccessKeyLastUsed"
- "iam:GetAccountAuthorizationDetails"
- "iam:ListAccessKeys"
- "iam:ListAttachedRolePolicies"
- "iam:ListAttachedUserPolicies"
- "iam:ListEntitiesForPolicy"
- "iam:ListGroupPolicies"
- "iam:ListGroups"
- "iam:ListGroupsForUser"
- "iam:ListInstanceProfilesForRole"
- "iam:ListInstanceProfiles"
- "iam:GetInstanceProfile"
- "iam:ListMFADevices"
- "iam:ListPolicies"
- "iam:ListRolePolicies"
- "iam:ListRoleTags"
- "iam:ListRoles"
- "iam:ListUserPolicies"
- "iam:ListUserTags"
- "iam:ListUsers"
- "iam:ListVirtualMFADevices"
- "iam:ListServerCertificates"
- "iam:ListAccountAliases"
- "kinesis:ListStreams"
- "kinesis:DescribeStream"
- "kms:DescribeKey"
- "kms:GetKeyPolicy"
- "kms:GetKeyRotationStatus"
- "kms:ListAliases"
- "kms:ListGrants"
- "kms:ListKeys"
- "network-firewall:ListFirewallPolicies"
- "network-firewall:ListFirewalls"
- "network-firewall:ListRuleGroups"
- "network-firewall:DescribeFirewall"
- "network-firewall:DescribeFirewallPolicy"
- "network-firewall:DescribeRuleGroup"
- "lambda:GetFunctionConfiguration"
- "lambda:GetFunctionEventInvokeConfig"
- "lambda:GetPolicy"
- "lambda:ListFunctions"
- "lambda:ListEventSourceMappings"
- "logs:DescribeLogGroups"
- "logs:DescribeMetricFilters"
- "rds:DescribeDBClusterSnapshotAttributes"
- "rds:DescribeDBClusterSnapshots"
- "rds:DescribeDBClusters"
- "rds:DescribeDBInstances"
- "rds:DescribeDBParameterGroups"
- "rds:DescribeDBParameters"
- "rds:DescribeDBSecurityGroups"
- "rds:DescribeDBSnapshotAttributes"
- "rds:DescribeDBSnapshots"
- "rds:DescribeDBSubnetGroups"
- "rds:DescribeEventSubscriptions"
- "rds:ListTagsForResource"
- "redshift:DescribeClusterParameterGroups"
- "redshift:DescribeClusterParameters"
- "redshift:DescribeClusterSecurityGroups"
- "redshift:DescribeClusterSubnetGroups"
- "redshift:DescribeClusters"
- "redshift:DescribeLoggingStatus"
- "route53:GetHostedZone"
- "route53:ListHostedZones"
- "route53:ListResourceRecordSets"
- "route53:ListTagsForResource"
- "route53domains:ListDomains"
- "s3:GetAccountPublicAccessBlock"
- "s3:GetBucketAcl"
- "s3:GetBucketLocation"
- "s3:GetBucketLogging"
- "s3:GetBucketNotification"
- "s3:GetBucketObjectLockConfiguration"
- "s3:GetBucketOwnershipControls"
- "s3:GetBucketPolicy"
- "s3:GetBucketPublicAccessBlock"
- "s3:GetBucketTagging"
- "s3:GetBucketVersioning"
- "s3:GetBucketWebsite"
- "s3:GetEncryptionConfiguration"
- "s3:GetLifecycleConfiguration"
- "s3:GetReplicationConfiguration"
- "s3:ListAllMyBuckets"
- "sagemaker:ListNotebookInstances"
- "sagemaker:DescribeNotebookInstance"
- "sagemaker:DescribeNotebookInstanceLifecycleConfig"
- "secretsmanager:ListSecrets"
- "secretsmanager:DescribeSecret"
- "securityhub:DescribeHub"
- "ses:GetIdentityDkimAttributes"
- "ses:GetIdentityPolicies"
- "ses:ListIdentities"
- "ses:ListIdentityPolicies"
- "states:ListStateMachines"
- "states:DescribeStateMachine"
- "ssm:DescribeParameters"
- "ssm:GetParameters"
- "ssm:ListComplianceItems"
- "ssm:ListDocuments"
- "ssm:DescribeDocument"
- "ssm:DescribeDocumentPermission"
- "ssm:DescribeInstanceInformation"
- "sns:GetTopicAttributes"
- "sns:GetSubscriptionAttributes"
- "sns:ListSubscriptions"
- "sns:ListSubscriptionsByTopic"
- "sns:ListTopics"
- "sqs:GetQueueAttributes"
- "sqs:GetQueueUrl"
- "sqs:ListQueues"
- "waf:ListActivatedRulesInRuleGroup"
- "waf:ListRuleGroups"
- "waf:ListRules"
- "waf:ListWebACLs"
- "waf:GetLoggingConfiguration"
- "waf:GetRateBasedRule"
- "waf:GetRuleGroup"
- "waf:GetRule"
- "waf:GetWebACL"
- "wafv2:ListWebACLs"
- "wafv2:GetWebACL"
- "wafv2:GetWebACLForResource"
- "wafv2:GetLoggingConfiguration"
- "wafv2:ListIPSets"
- "wafv2:GetIPSet"
- "wafv2:ListRuleGroups"
- "wafv2:GetRuleGroup"
- "waf-regional:ListActivatedRulesInRuleGroup"
- "waf-regional:ListWebACLs"
- "waf-regional:ListRuleGroups"
- "waf-regional:ListRules"
- "waf-regional:GetLoggingConfiguration"
- "waf-regional:GetRateBasedRule"
- "waf-regional:GetRuleGroup"
- "waf-regional:GetRule"
- "waf-regional:GetWebACL"
- "tag:Get*"
Resource: "*"
- Effect: "Allow"
Action:
- "s3:GetObject"
Resource:
- "arn:aws:s3:::elasticbeanstalk-env-resources-*/*"
Condition:
StringNotLike:
"s3:ResourceAccount": !Ref "AWS::AccountId"
ShishoCloudOpenIdConnectProvider:
Type: "AWS::IAM::OIDCProvider"
Properties:
Url: "https://tokens.cloud.shisho.dev"
ClientIdList:
- "sts.amazonaws.com"
ThumbprintList:
- "9e99a48a9960b14926bb7f3b02e22da2b0ab7280"
IAM ロールが作成できたら、その ARN を控えてください。ARN は上記の標準設定例の場合、arn:aws:iam::123456789012:role/ShishoCloudSecurityAudit のようになるはずです。
Shisho Cloud への ARN の登録
「歯車マーク ⚙ > 連携(Integrations)」画面に表示されているカード「AWS」の「設定」ボタンを押下し、画面の指示に従いながら ARN を入力してください。
入力が完了すると、設定ページに、以下のようなチェックマークと共に ARN が表示されるはずです:
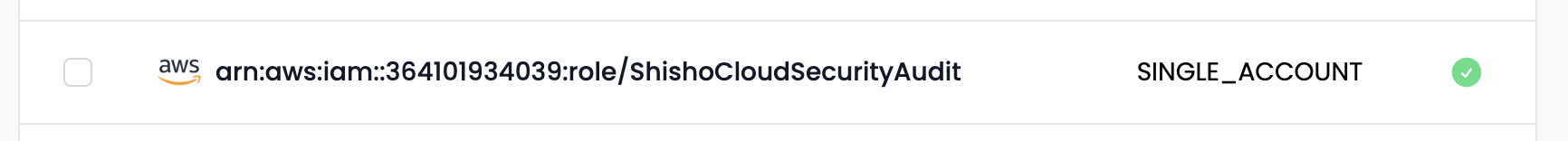
この状態になれば AWS 連携のセットアップは完了です。Shisho Cloud は AWS のアカウントにアクセスできるようになっています。
AWS 側のキャッシュ仕様の兼ね合いで、連携後数分間は Shisho Cloud が AWS にアクセスできない可能性があります。 直ちに設定が完了しない場合は、最大 5 分程度お待ちください。
もし上記の手順で AWS 連携が正常に行えない場合は、遠慮なくサービス運営元(Flatt Security)にお問い合わせください。
参考: 連携の解除方法
連携を解除する際は、Shisho Cloud 上での作業の他、以下の AWS のリソースを削除してください。
- IAM ロール
ShishoCloudSecurityAudit - ID プロバイダ
https://tokens.cloud.shisho.dev