Organization Verification and Ownership Verification
The English user guide is currently in beta preview. Most of the documents have been automatically translated from the Japanese version. Should you find any inaccuracies, please reach out to Flatt Security.
Overview
In order to use features which involve dynamic network connections (such as Takumi's blackbox assessment), users must first complete either the Organization Authentication or the Ownership Verification process.
Organization Authentication
Organization Authentication is the process of linking a Shisho Cloud organization with information regarding the enterprise which is using it.
To authenticate an organization, an application must be submitted by the user, to be approved by the provider (GMO Flatt Security). Approval takes approximately 2-3 business days.
Upon approval, the use of features which involve dynamic network connections against targets such as production environments (such as Takumi's blackbox assessment) will be available for use without the need of per-target ownership verification.
Regardless of the authentication state of an organization, users must adhere to and comply with the terms of use, as well as laws and regulations when using features which involve dynamic network connections against targets such as production environments.
A given Shisho Cloud organization may only have one enterprise linked to it. However, use cases involving multiple entities are supported, including the following scenarios, provided that users comply with the terms of use (including ensuring lawful rights for usage and ensuring that relevant employees are informed of and comply with the terms):
- The linked enterprise uses the Shisho Cloud organization on behalf of other entities (e.g., a security consulting firm conducting assessments for clients)
- The linked enterprise allows other entities to use the Shisho Cloud organization through arrangements such as outsourcing (e.g., for governance purposes among affiliated companies)
Per-Target Ownership Verification
If authenticating your organization is difficult at the moment (e.g., for individual use), you can still use features that involve dynamic network connections to production environments by proving ownership of the target application.
If your organization is already authenticated, you can use features that involve dynamic network connections without per-target ownership verification.
Please note that only users with either the organization owner role or the Takumi manager role is able to conduct per-target ownership verification. Users without those roles are still able to dispatch Takumi Blackbox assessments against already-verified target apps, but will not have access to the ownership verification token or the verification form.
If you enter a target URL for an app that has not been verified, an error will be displayed and the assessment cannot be dispatched.
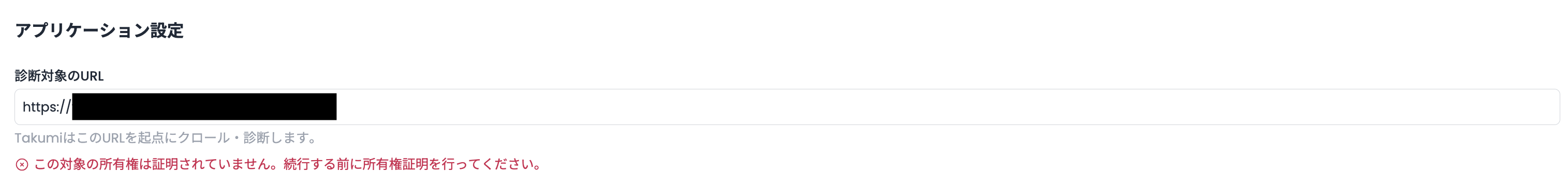
Ownership Verification Steps
To verify ownership of a target to scan, scroll to the Verify Ownership of New Target section below the Target URL input. There, you will be able to access the token to be used to verify ownership of your target application.
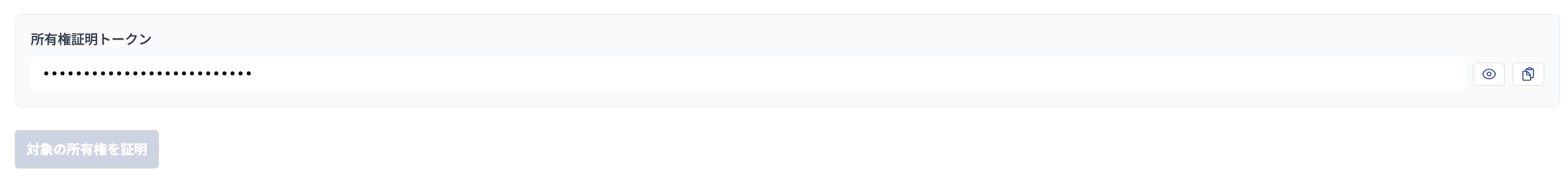
Store this verification token in one of the following two ways and proceed with the verification process:
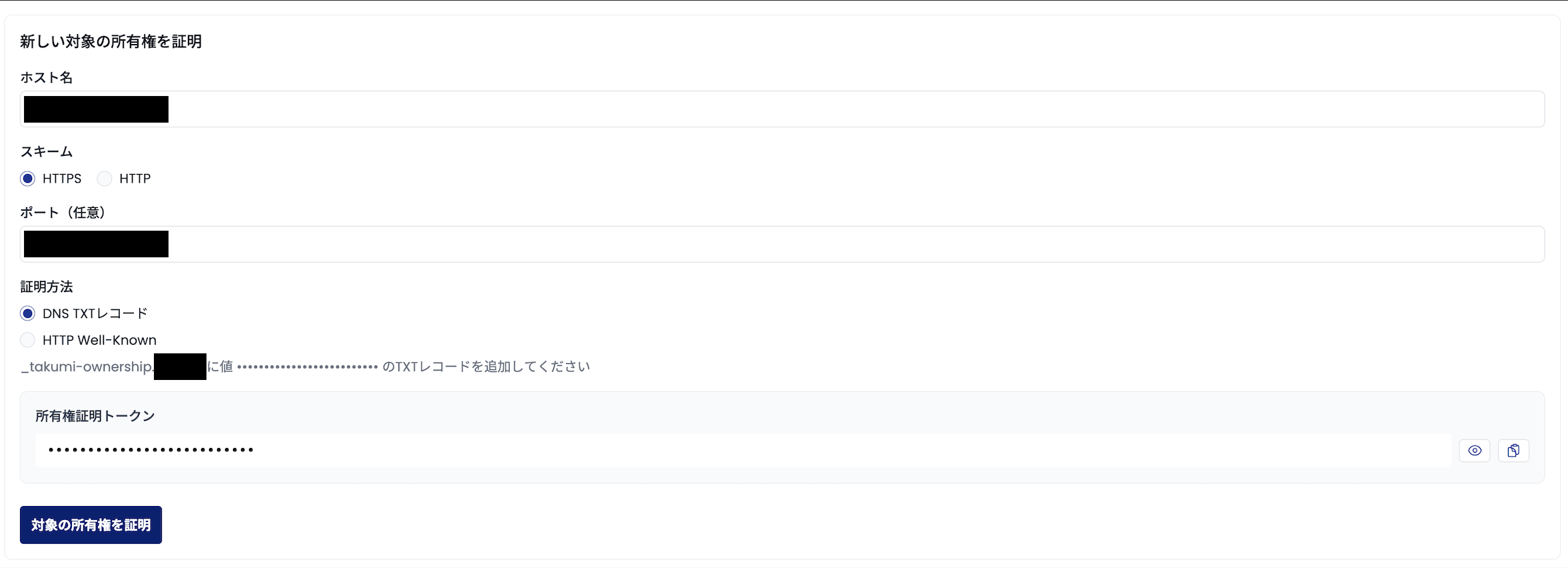
1) DNS TXT Record Verification
Add a DNS TXT record to the subdomain _takumi-ownership.<your-domain> with your verification token as the value.
For example, if your target domain is example.com and your token is 0123ABCD, create a TXT record for _takumi-ownership.example.com with the value 0123ABCD.
Once configured, select "DNS TXT Record" as the verification method in the Target Ownership Verification section, enter your hostname, and click "Verify Target".
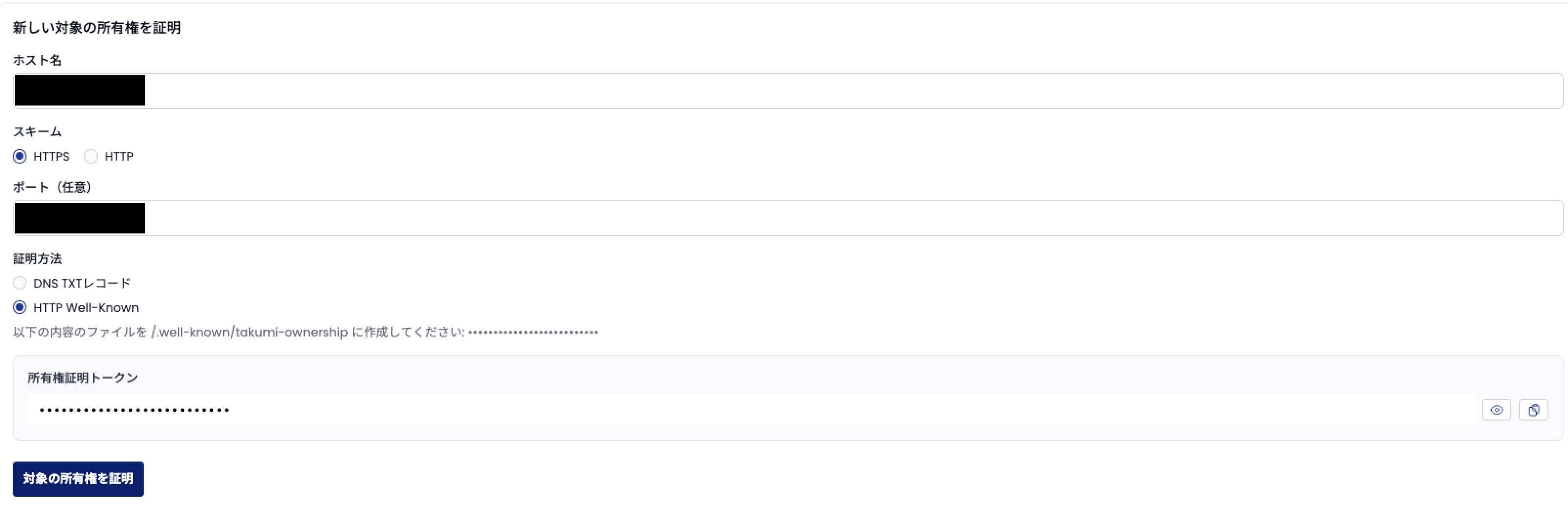
2) HTTP Well-Known Directory Verification
Create a file at the well-known path /.well-known/takumi-ownership on your target server containing just your verification token as the file content.
For example, in order to validate the target https://example.com with the token 0123ABCD, create a file at https://example.com/.well-known/takumi-ownership. The file must contain just the token 0123ABCD, and no other data.
The file containing the token must be accessible via HTTP/HTTPS connection, and the token must be returned as plaintext with a 200 OK response.
Once configured, select "HTTP Well-Known" as the verification method in the Target Ownership Verification section, enter your hostname, and click "Verify Target".
Note that if you do not specify the port number, it will default to either port 443 for HTTPS, and port 80 for HTTP.
Confirming Verification State
Once you click Verify Target Ownership, you should get a response on the outcome of the verification, and the Target Ownership Verification State section below should be updated with the verification state of the target you specified.
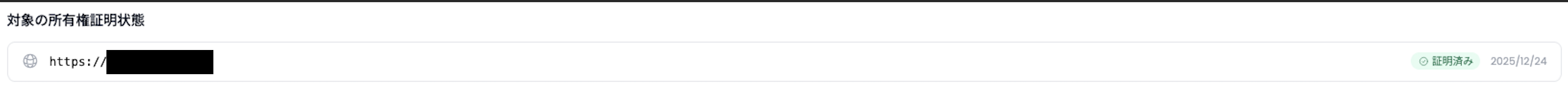
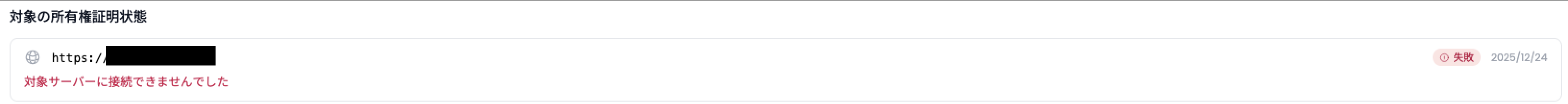
Note that, should verification fail, the reason for the most recent verification failure for any given target will be displayed in the same section. In the case of unknown or unexpected errors being returned, please contact us.
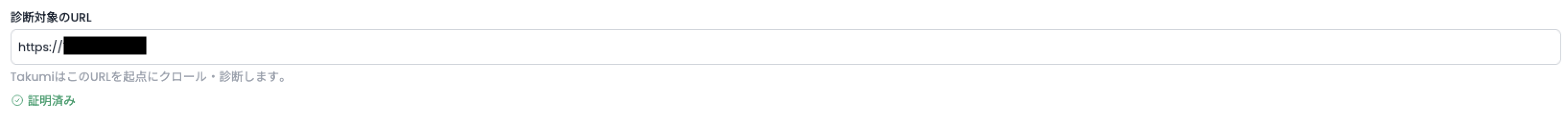
After verification, users are able to input their verified target apps in the Target URL section, and proceed with dispatching the assessment.
There is a 10-second cooldown after attempting to verify the same target. Please wait before trying again.
If verification succeeds but the target still shows as unverified when entered in the "Target URL" field, please reload the assessment creation page and try again.