Invite Takumi to Slack
The English user guide is currently in beta preview. Most of the documents have been automatically translated from the Japanese version. Should you find any inaccuracies, please reach out to Flatt Security.
This feature is currently available only to selected organizations.
What is Takumi
 Takumi is an AI agent built to support human product engineers and security engineers.
It identifies and fixes vulnerabilities, triages findings, and assists with secure design — all within your Slack workspace.
Takumi is an AI agent built to support human product engineers and security engineers.
It identifies and fixes vulnerabilities, triages findings, and assists with secure design — all within your Slack workspace.
If you don't use Slack, please check out How to chat with Takumi in Shisho Cloud byGMO.
Required Settings to Invite Takumi to Slack
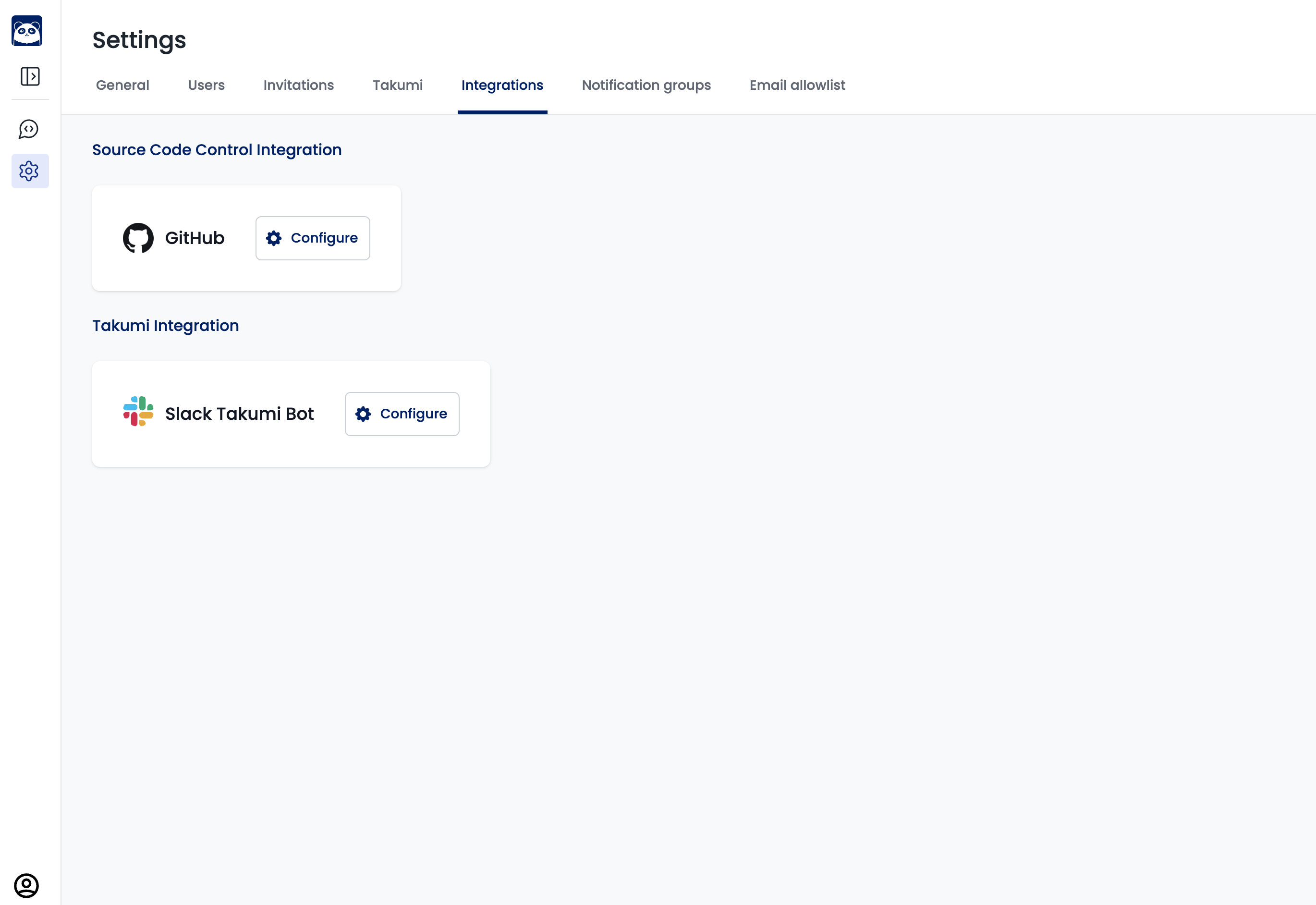
To enable Takumi to assess private repositories on GitHub via Slack, you need "Slack Integration" and "GitHub Integration" in the "Settings > Integrations" tab, and then set up data scope per Slack channel (/takumi-scopes).
1. How to Set Up Slack Integration

Takumi needs to be invited to your Slack workspace as a Slack App. You can connect your Slack workspace under "Settings > Integrations > Takumi Integration":
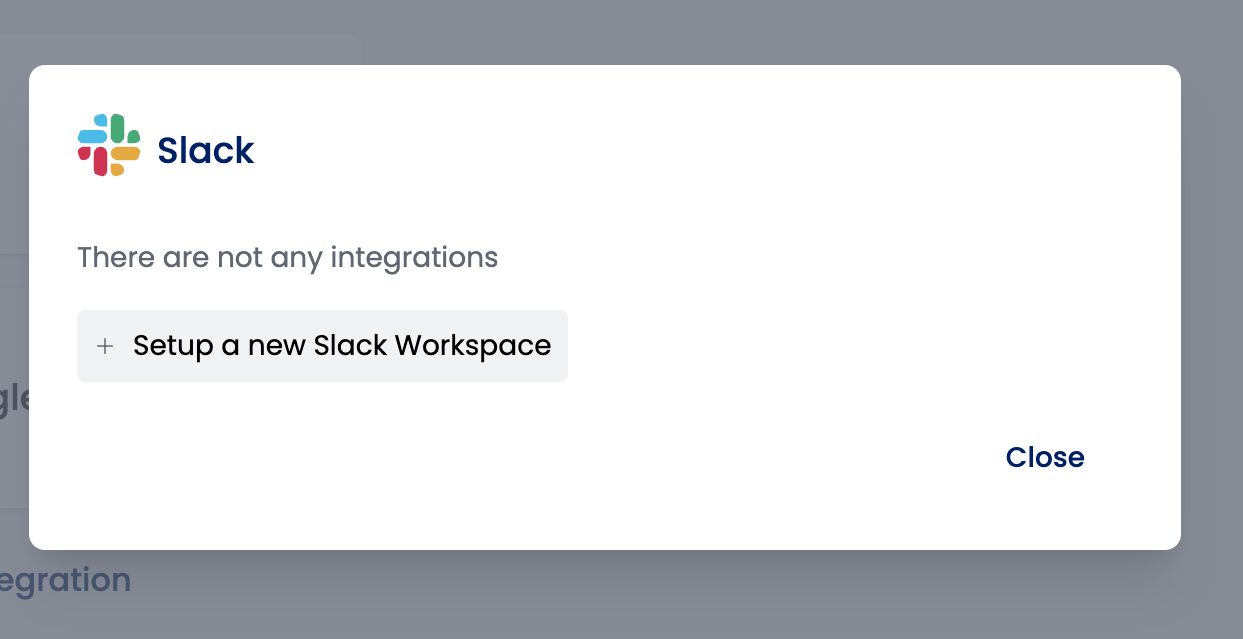
Click on "Set up a new Slack workspace" to be redirected to a screen provided by Slack. Review the details carefully and click "Allow":

After clicking, the connection between your Slack workspace and Shisho Cloud byGMO will be completed. If successful, the Slack workspace should appear as shown below:
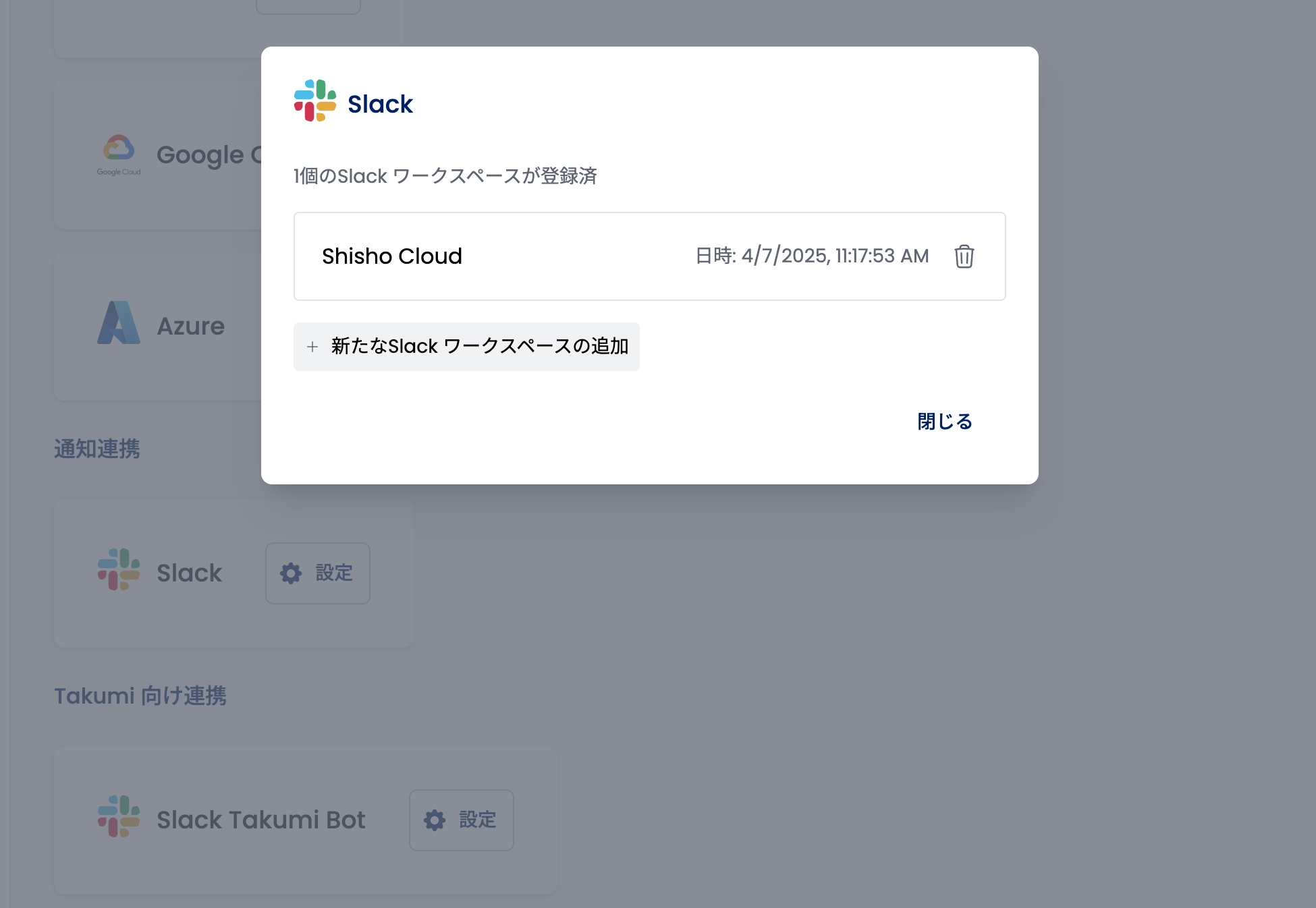
When performing this operation, approval from the Slack workspace owner may be required. In that case, please contact the Slack workspace owner and request approval for the Slack App.
After the Slack App integration is approved, please perform the Slack workspace and Shisho Cloud connection process again from the Shisho Cloud screen.
If you have issues with Slack integration, please check "About Slack Integration" or refer to the Slack Help Center.
2. How to Set Up GitHub Integration
When you connect Takumi to your GitHub organization, Takumi can assess private repositories as well. Please set up GitHub integration by referring to the "Integrations > GitHub" guide.
Once you've completed both Slack and GitHub integrations, add Takumi to your preferred channel and start requesting assessments!
3. How to Set Up data scope per Slack channel
After integrating your Slack and GitHub, the repository to request an assessment for must be included as the scope. Refer to the "Using Takumi Slack Commands" guide to add repositories to Takumi's scope.
How to Use Takumi
Get the Most Out of Takumi
Check the guide: Getting the Most Out of Takumi.
Stop Takumi's Task
If you type SLEEP, Takumi will pause the current task.
Takumi has ability to detect vulnerabilities with high accuracy through deep analysis. When investigating an entire repository, it may continue the investigation for several hours.
Optional Configuration Items
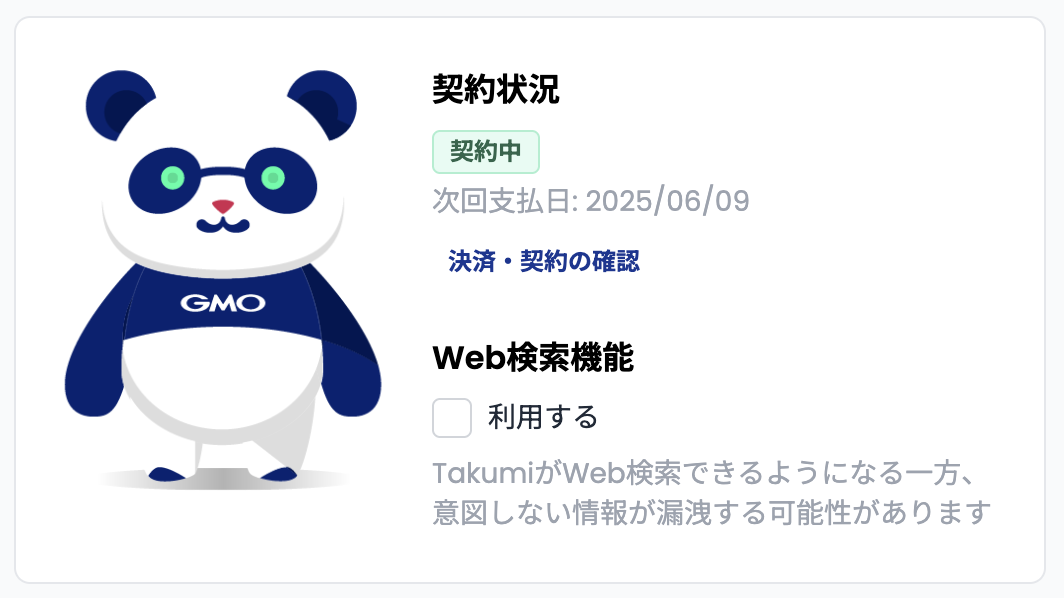
"Web Search Feature" Option
We recommend turning OFF the "Web Search Feature" option.
When the "Web Search Feature" option is enabled, Takumi will flexibly search for information on the internet by operating a browser as needed during the audit process. By default, this is turned off, and Takumi will not operate a browser.
Reasons for Recommending Disabling This Option
Even with the "Web Search Feature" option turned OFF, Takumi can handle many security tasks.
This is because Takumi is provided with safe access methods not only to the source code, but also to GitHub Issues, Pull Requests, vulnerability databases, and other sources.
The "Web Search Feature" is a means for having Takumi investigate sources other than these information sources.
For the following reasons, we recommend turning OFF Takumi's "Web Search Feature" option.
-
Risk of information leakage due to Takumi's unexpected browser operations:
With the "Web Search Feature", we cannot eliminate the possibility that Takumi might input your confidential information (code, prompts, etc.) or information derived from them to external sites through search queries or form inputs that may occur during browser operations.Note that when the "Web Search Feature" is off, the operations for accessing external information (similar to function calling / tool use) have limited access to the network; it is restricted to the scope where we can guarantee that the arguments of operations do not contain such confidential information (or information directly derived from them).1
-
Impact on running time and credit consumption:
When Takumi uses a browser during the audit process, the running time and credit consumption tend to increase. For tasks that can be accomplished even with the "Web Search Feature" turned off, keeping this option off can suppress these increases.
Footnotes
-
For example, the "tool to get details from CVE ID" allows strict validation of arguments because the CVE ID format is restrictive. Also, the "tool to list known vulnerability information (CVE IDs, etc.) in dependencies" safely matches vulnerability databases with used packages within Takumi's execution environment. These tools access external information safely, and thus are provided to Takumi even when the "Web Search Feature" is off. ↩